¶ 1) Create a dedicated member in your Active Directory
The Kerberos method of the HaCluster can be used without need to use an Administrator account.
In this case, you need to create a member inside your Active Directory and generates the dedicated keytab.
|
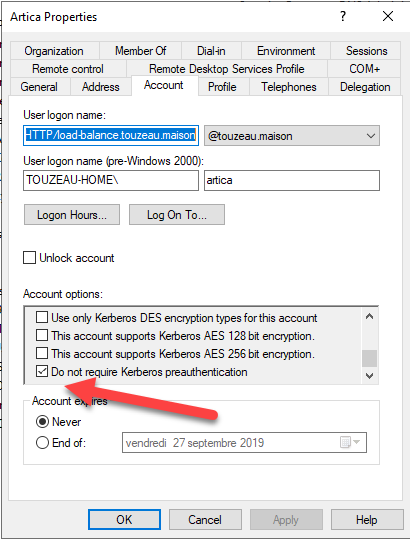
Just create a dedicated account for example named “Artica” Enable extra options on this user:
Ensure that your load-balancer IP address and reverse record is added in your Active Directory DNS.
|
 |
¶ 2) Fill general information inside Artica Web-console
With Artica 4.30 SP429 a new feature as been added that allows you to make a connection with a wizard
- This operation must be made on the load balancer.
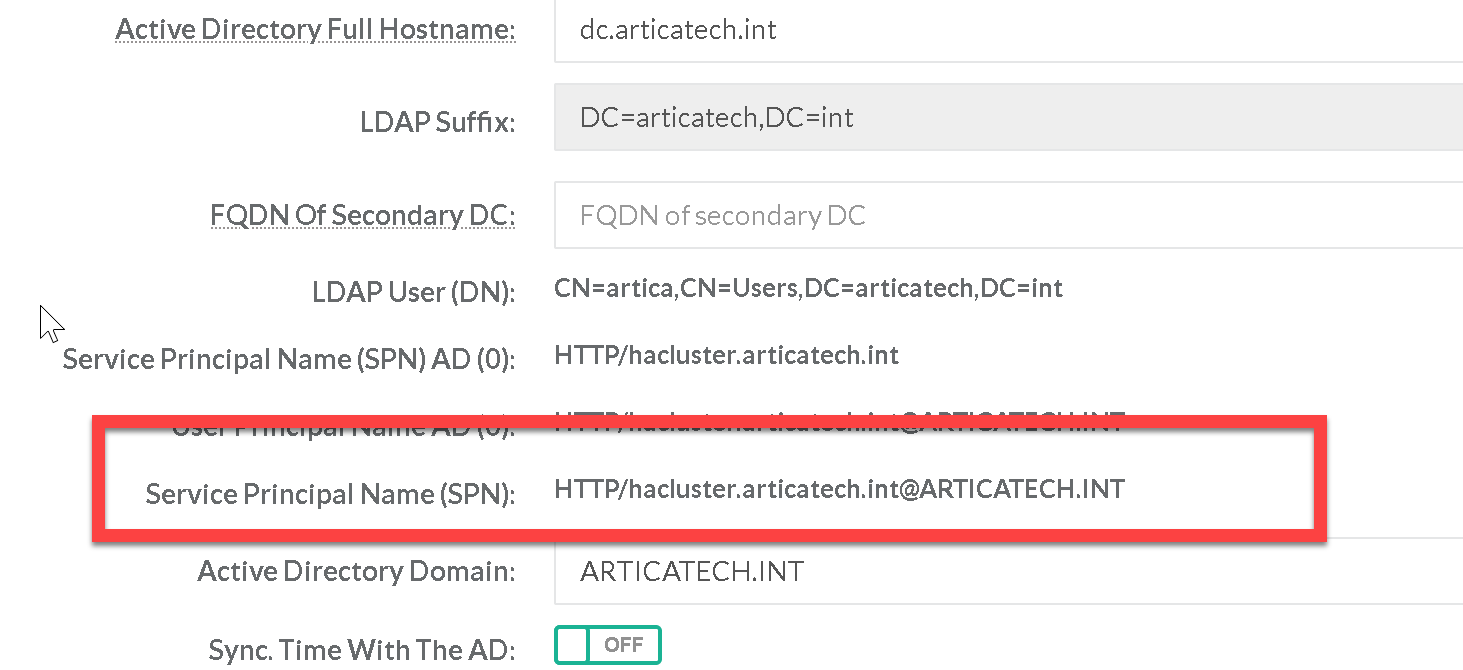
- The left menu “HaCluster” / “Active Directory” allows you to define parameters to enable Active Directory connections on backend servers.
- Check the standard Active Directory “Prerequisites” section before using this section
Not for the load balancer itself:
The load balancer is able to send Active Directory information to backends.
You don't have to set anything on the backends proxies themselves
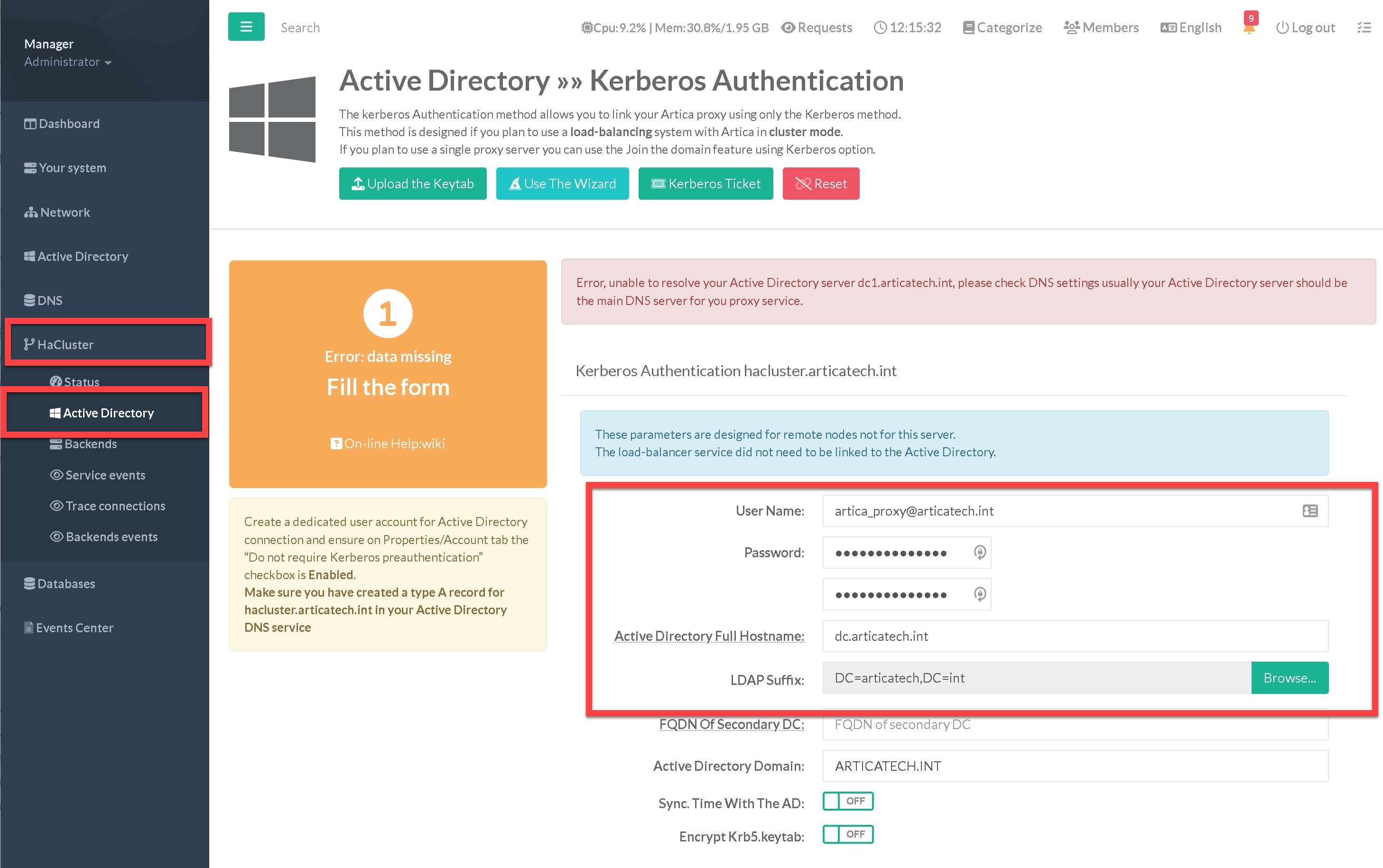
- Fill the form correctly (using prerequisites for the used account used)
- If you want to secure exchange the krb5.keytab between servers, click on Crypt Krb5.keytab checkbox
¶ 3) Generate the keytab file on the AD
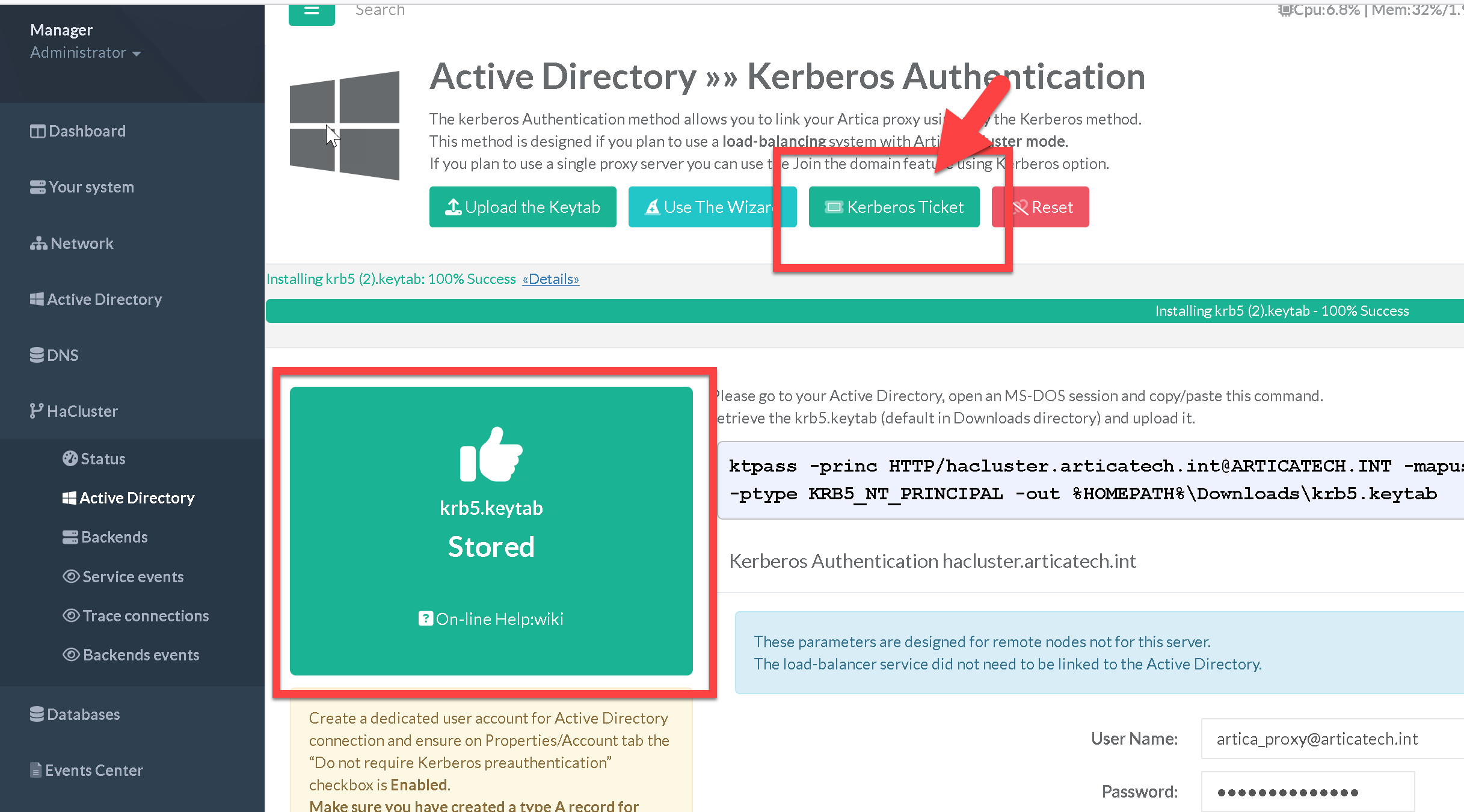
- After the form filled, you will see a section that allows you explain how to run a command line in your Active Directory in order to get the Kerberos ticket.
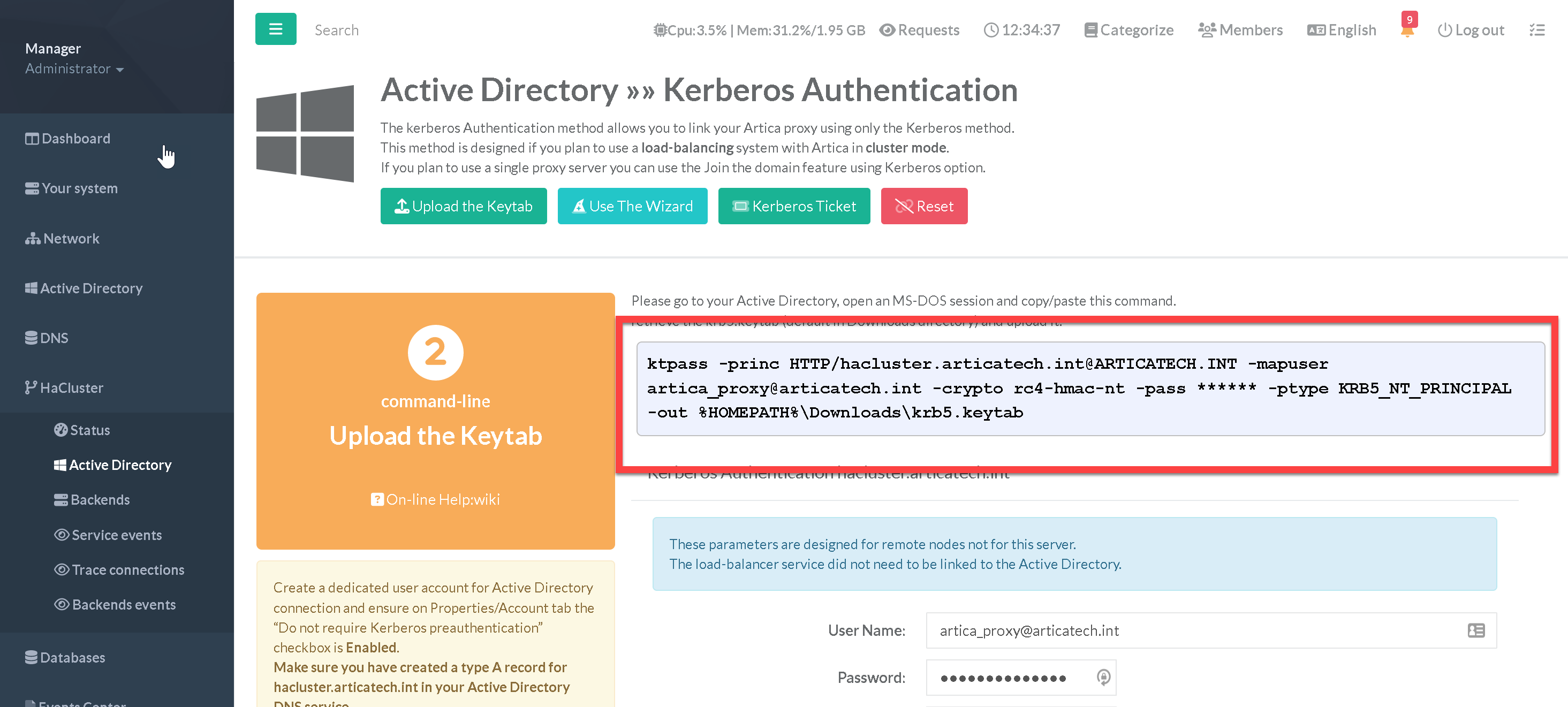
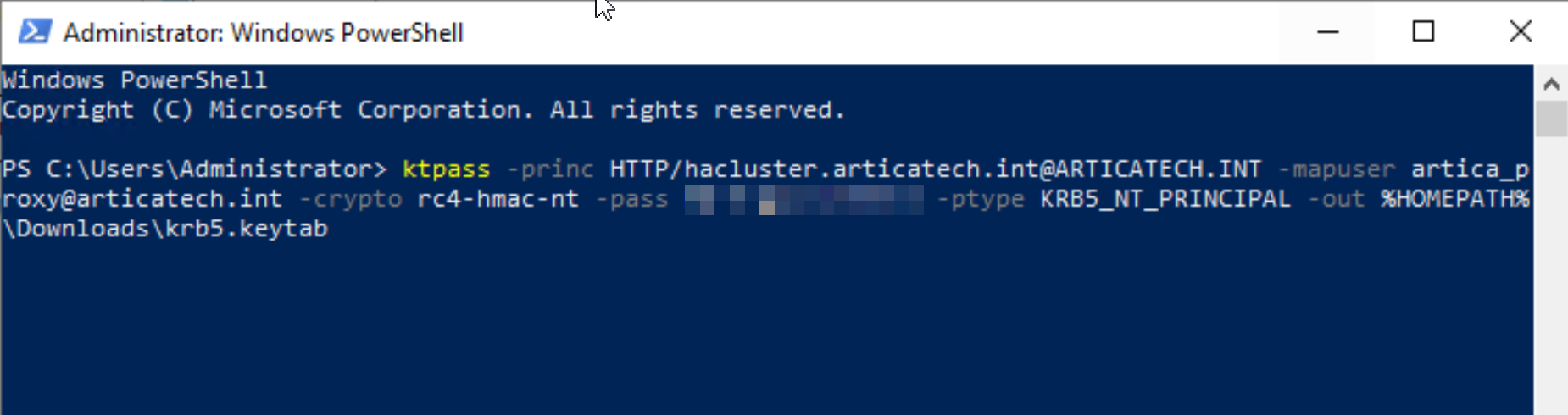
- In the command-line, replace
******by the real password of the created AD member.
$ to `$ )See:
- WARNING: Unable to set SPN mapping data
- Failed to write keytab file
- Adjusting Kerberos encryption types
¶ 4) Upload the keytab
- Get the generated keytab on the Active Directory and upload it using the top button “Upload the keytab”
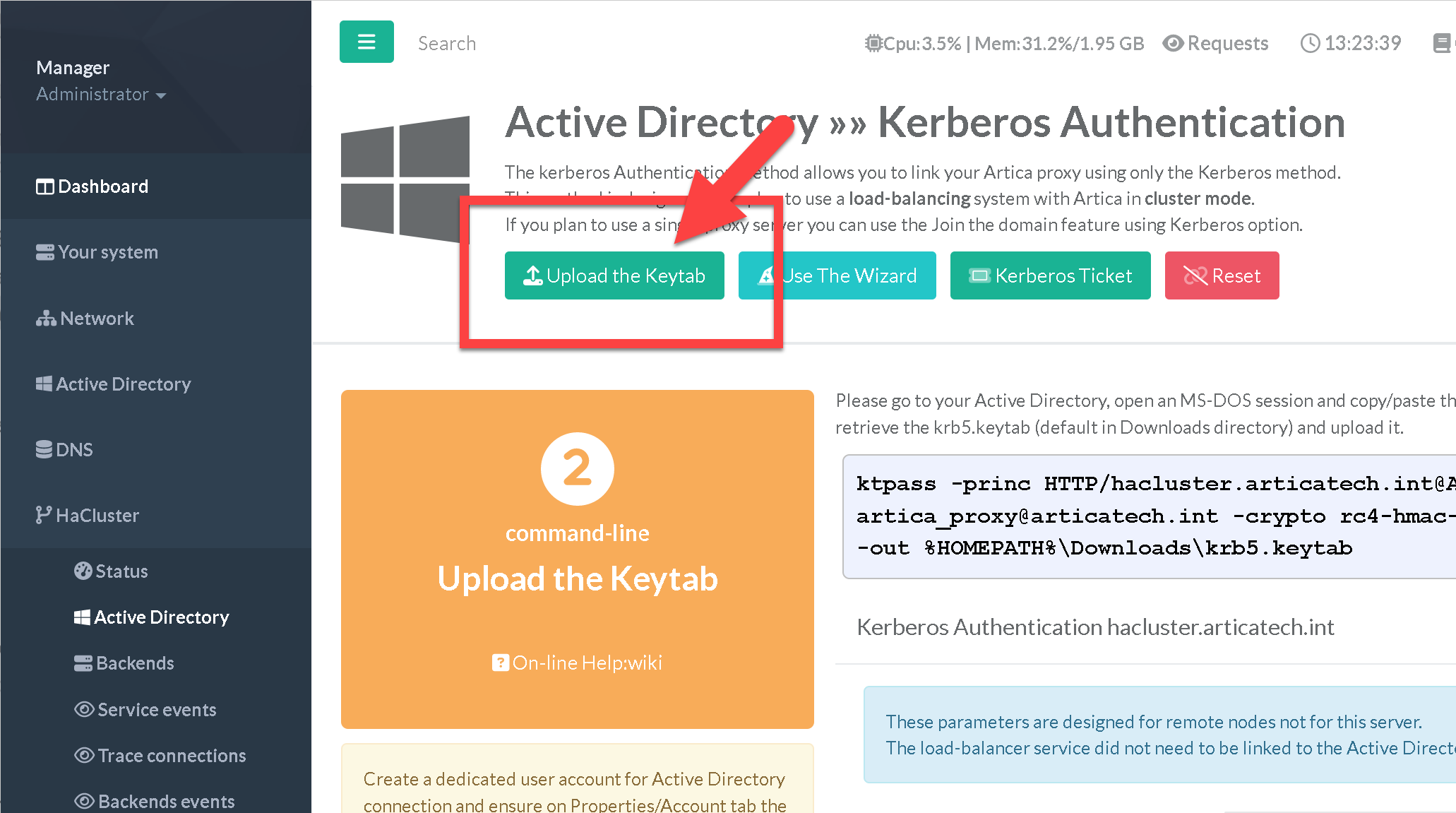
¶ 5) Verify the keytab
Once uploaded, click on the button “Kerberos Ticket”