Kerberos relies on time-limited tickets to verify identity without transmitting passwords. If a ticket is expired, malformed, or mismatched with the service keytab, authentication will fail — often silently, leading to frustrating "
access denied" errors for users and hard-to-diagnose issues for administrators.
Inspecting the validity of Kerberos tickets helps to:
- Ensure that tickets are not expired and have a valid "renew until" window.
- Confirm that the service principal in the ticket matches the proxy proxy's hostname and realm.
- Detect clock skew or domain controller issues that can silently invalidate tickets.
- Identify key version mismatches (KVNO) between Active Directory and the local keytab used by the proxy service.
- Verify that the authentication flow is working before deployment, reducing downtime and user impact.
This feature is available on Artica v4.50 Service Pack 3 or Artica v4.50 Service Pack 2 HotFix 20250515-21
In environments with tight security policies, this inspection also helps maintain compliance and prevent unauthorized access due to misconfigured or stale credentials.
In summary, validating Kerberos ticket status is essential for robust, reliable, and secure authentication when using Artica proxy with Active Directory.
- On the left menu, choose
Active Directory > Kerberos Authentication - On the left widget click on the “Information” button
- A new page is displayed and shows you Kerberos ticket information
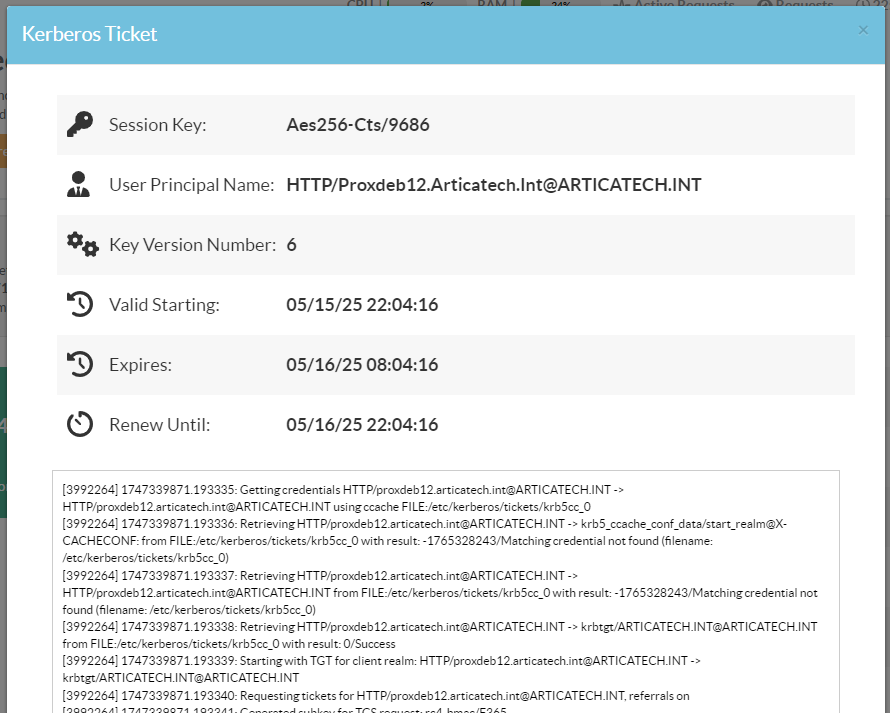
- Session Key:
The session key is a temporary, symmetric key generated by the Key Distribution Center (KDC) and shared securely between:
The client (e.g. a user or service)
The target service (e.g. HTTP/Artica, CIFS, LDAP, etc.)
This key is used to encrypt communications between the two parties during a Kerberos-authenticated session.
The session key is short-lived, unique to a login session.
It's different from the long-term keys stored in the keytab or in Active Directory.
Only the client and the service know this key, ensuring confidentiality and integrity of their communication.
- User Principal Name (UPN) is the unique identity used to authenticate a user across the Kerberos realm (or AD domain).
The UPN is how Kerberos identifies users during ticket requests (TGT,TGS, etc.)
UPN is also critical for cross-realm trust and federated authentication.
- Key Version Number.(kvno)
It is an integer that identifies the version of a cryptographic key associated with a Kerberos principal (such as a user or service).
When a key is changed (e.g., password reset, key rotation), a new encryption key is generated.
To distinguish it from the old key, the KVNO is incremented.
If the KVNO in the ticket doesn't match the KVNO in the service's keytab, authentication will fail with errors
- Valid starting:
Refers to the timestamp when the ticket becomes usable.
It is the beginning of the validity window for a Kerberos ticket.
This timestamp is set by the Key Distribution Center (KDC) and typically matches the moment the ticket is issued, unless there's a delay scheduled (e.g., for future use).
- Expires:
Refers to the timestamp when the ticket becomes invalid
That is, the moment after which the ticket will no longer be accepted by the service or KDC.
Once the expiration time is reached, The ticket cannot be used for authentication anymore and the connection to the Active Directory must be executed another time.
- Renew until indicates the latest possible time a renewable ticket can be extended without requiring the user to re-authenticate (e.g., re-enter a password).
It defines the maximum lifetime of the ticket across renewals.
You can renew the ticket before it expires, multiple times, up to this "renew until" time.