In Artica, administrators can establish a session in the Artica console based on their user accounts stored in a remote Active Directory or OpenLDAP server, or Artica's own OpenLDAP server, or via Artica's local database.
In this case, Artica provides Role-based access control (RBAC) feature that is a policy-neutral access-control mechanism defined around roles and privileges.
The components of RBAC such as role-permissions, user-role and role-role relationships make it simple to perform user assignments.
¶ In this article, we will focus on the "Proxy Monitor" privilege using an Active Directory database.
¶ A) Authorize Artica to identify users
In the Active Directory context, you must specify in the LDAP connections that the Active Directory connection is also authorized to check user accounts when connecting to the Artica login page.
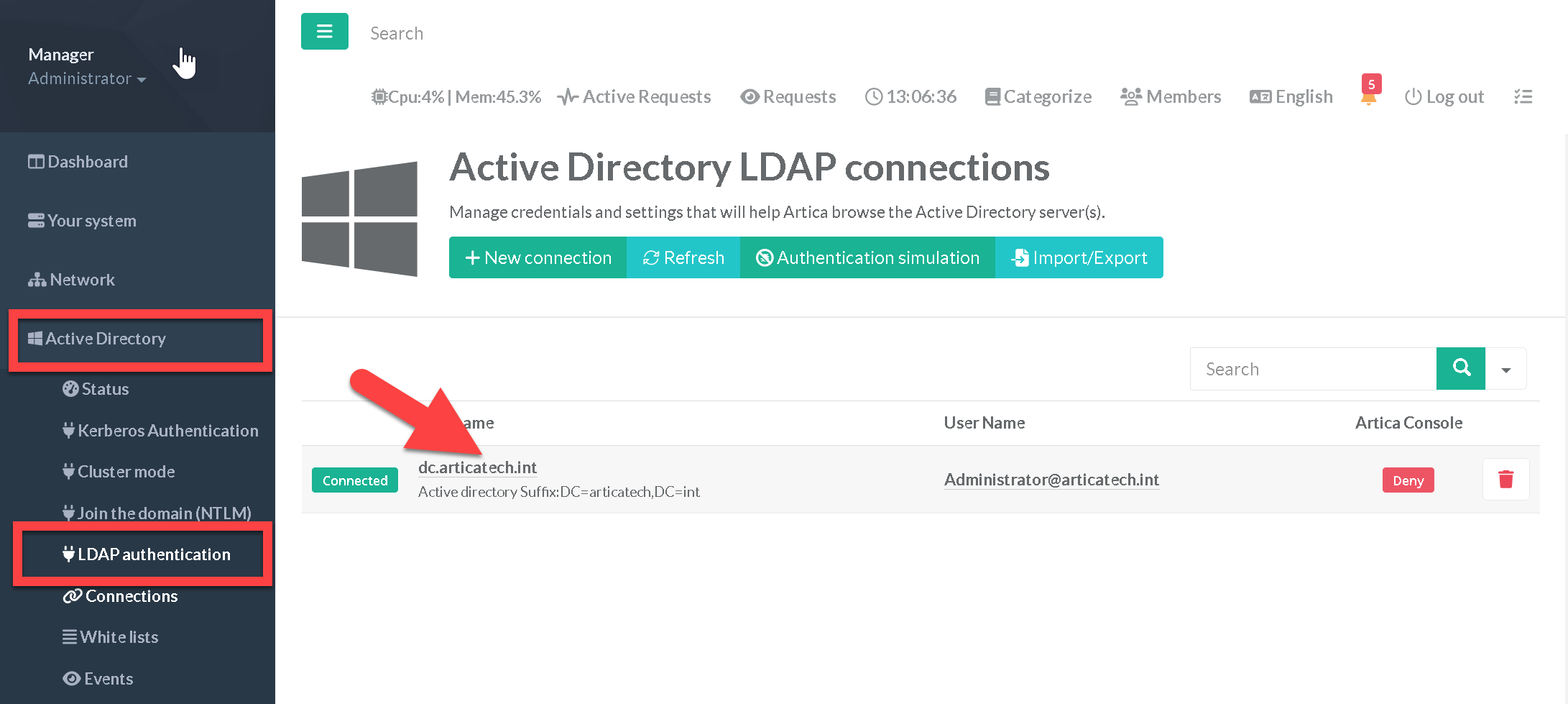
- In the left menu, go to
Active Directory > LDAP Authentication - Select your Active Directory connection
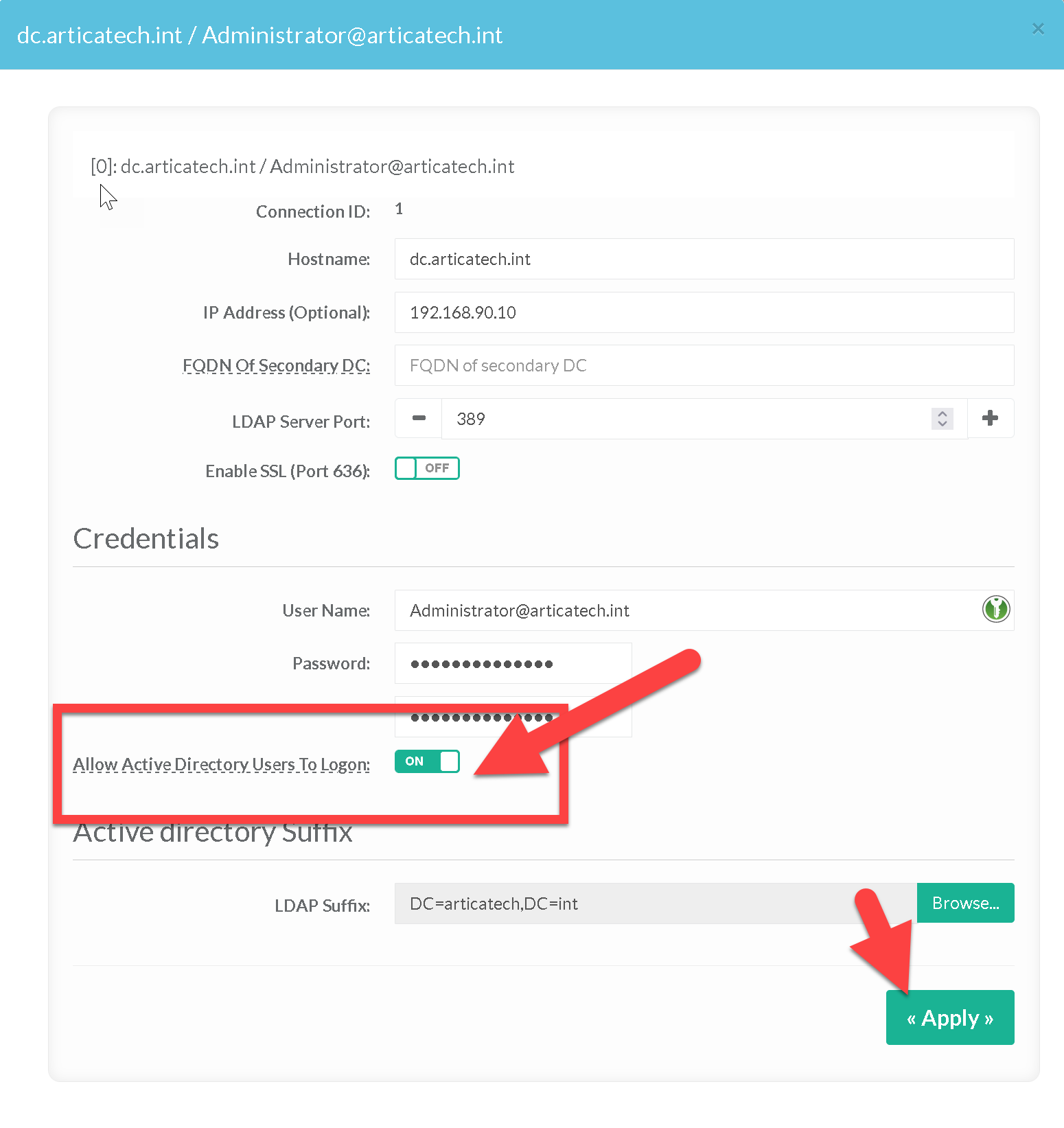
- Turn to ON the option “Allow Active Directory users to logon"
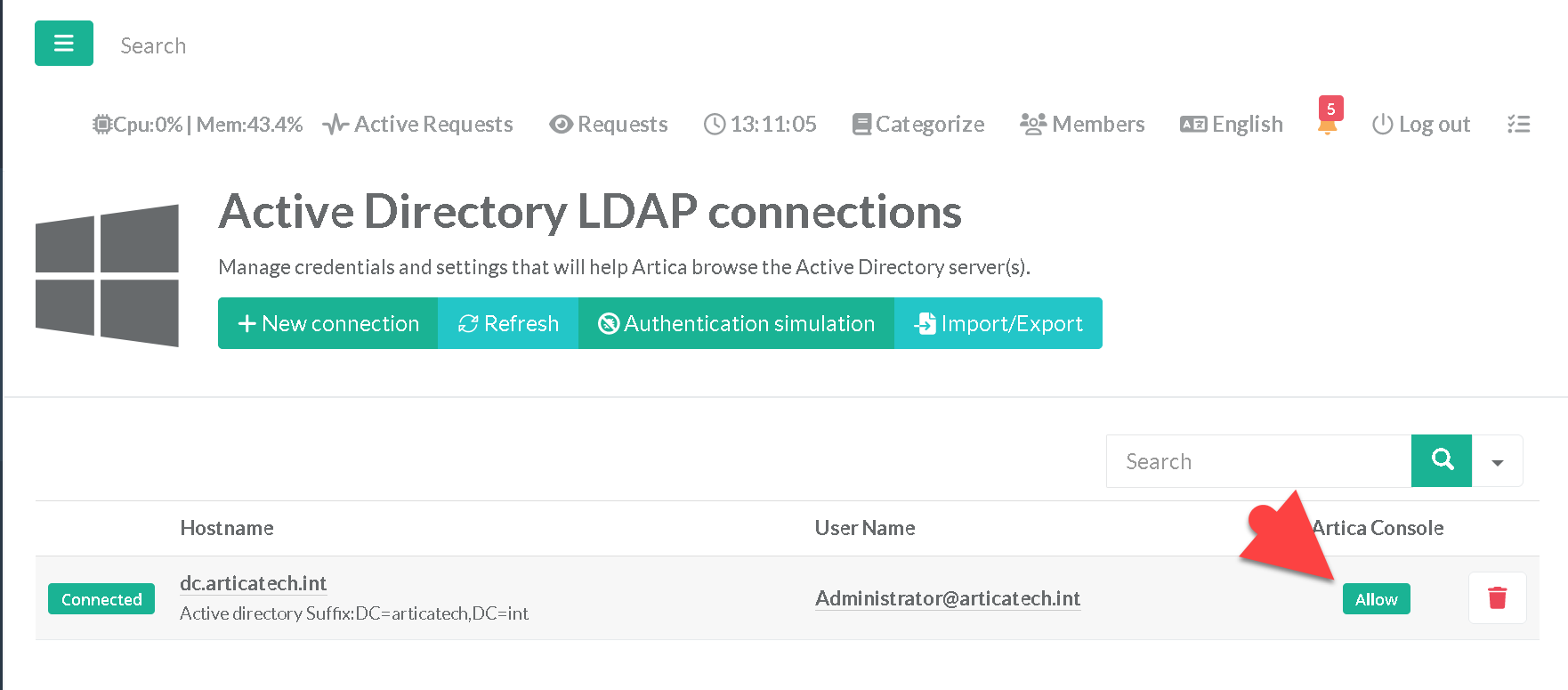
- In the main table, you will see a green icon “Allow” under your Active Directory connection.
¶ B) Dedicate a specific group.
Artica manages privileges according to user groups.
As the "Proxy Monitor" privilege is a restricted privilege, the best thing to do is to dedicate a user group for this purpose.
Please note that groups are cumulative.
If you assign an administrator to a group that has "Proxy Administrator" privileges and is also assigned to a "Proxy Monitor" group, the user will have both privileges, which will not restrict the user's rights.
In our case, we have created a group proxy_monitor inside the Active Directory database
¶ C) Search the group and assign the privilege
On the Artica Web console, click on the top menu “Members”
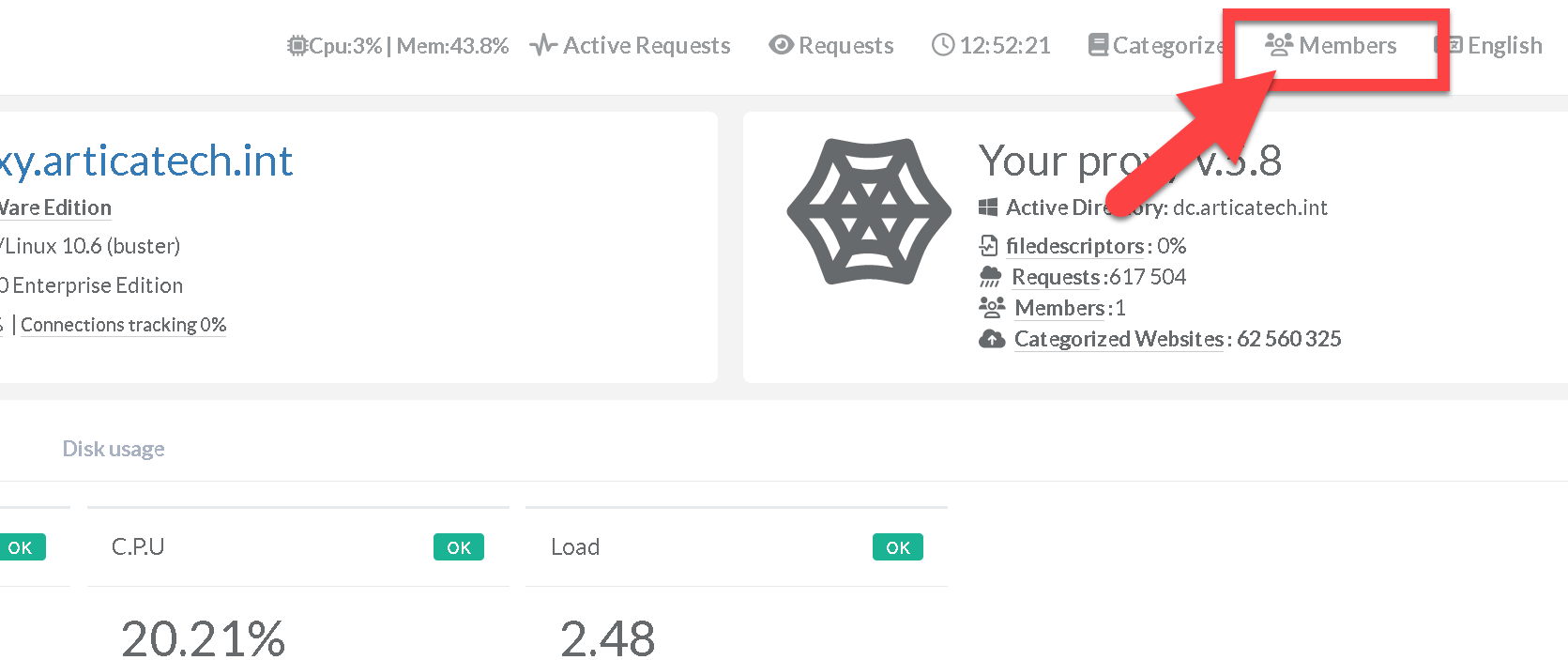
- Select the “Groups” button and search your group.
- Click on the group you want to assign the privilege
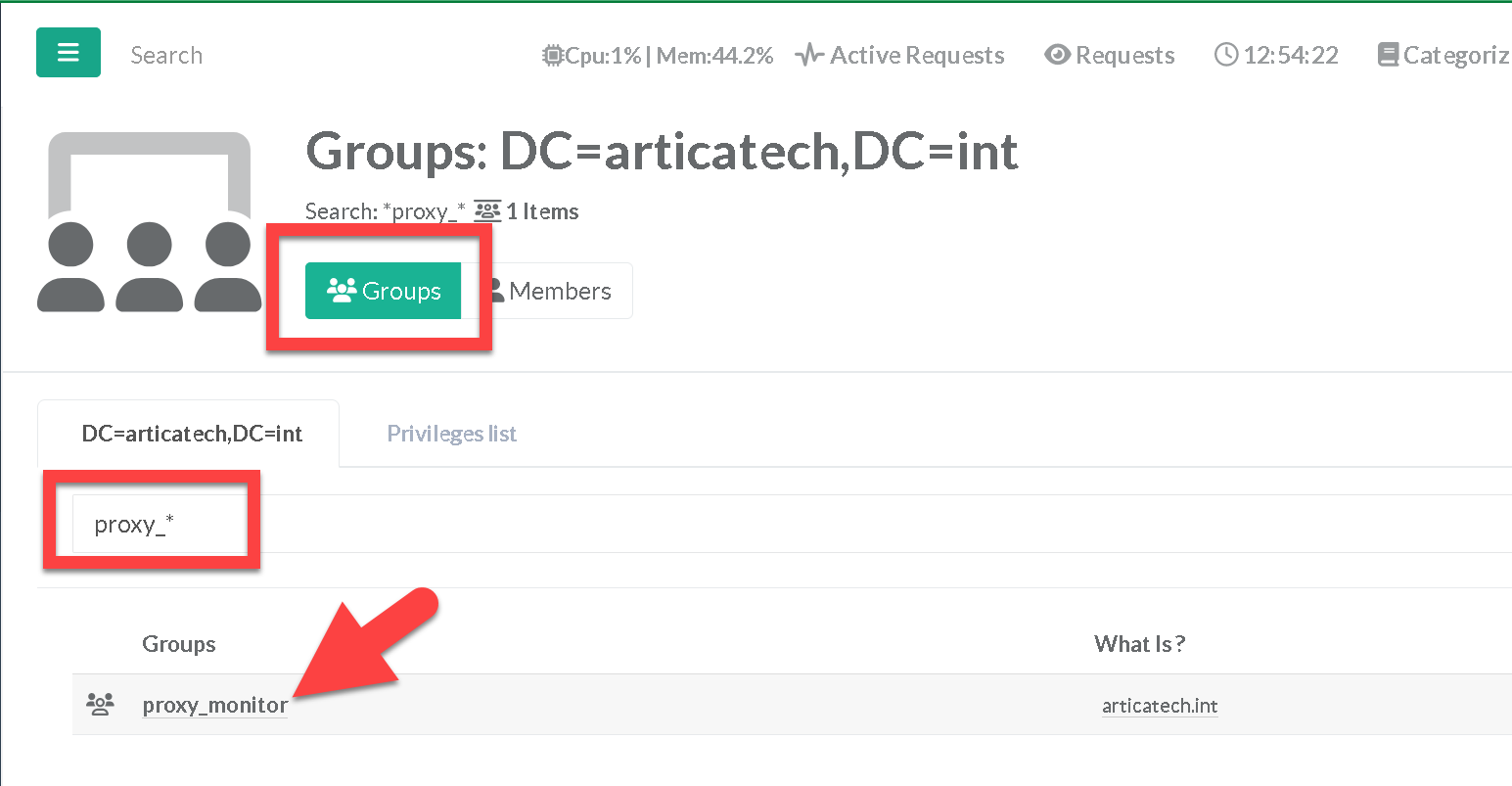
- Click on the “Privileges” tab and turn on only the “As Proxy Monitor” option.
- Click on Apply
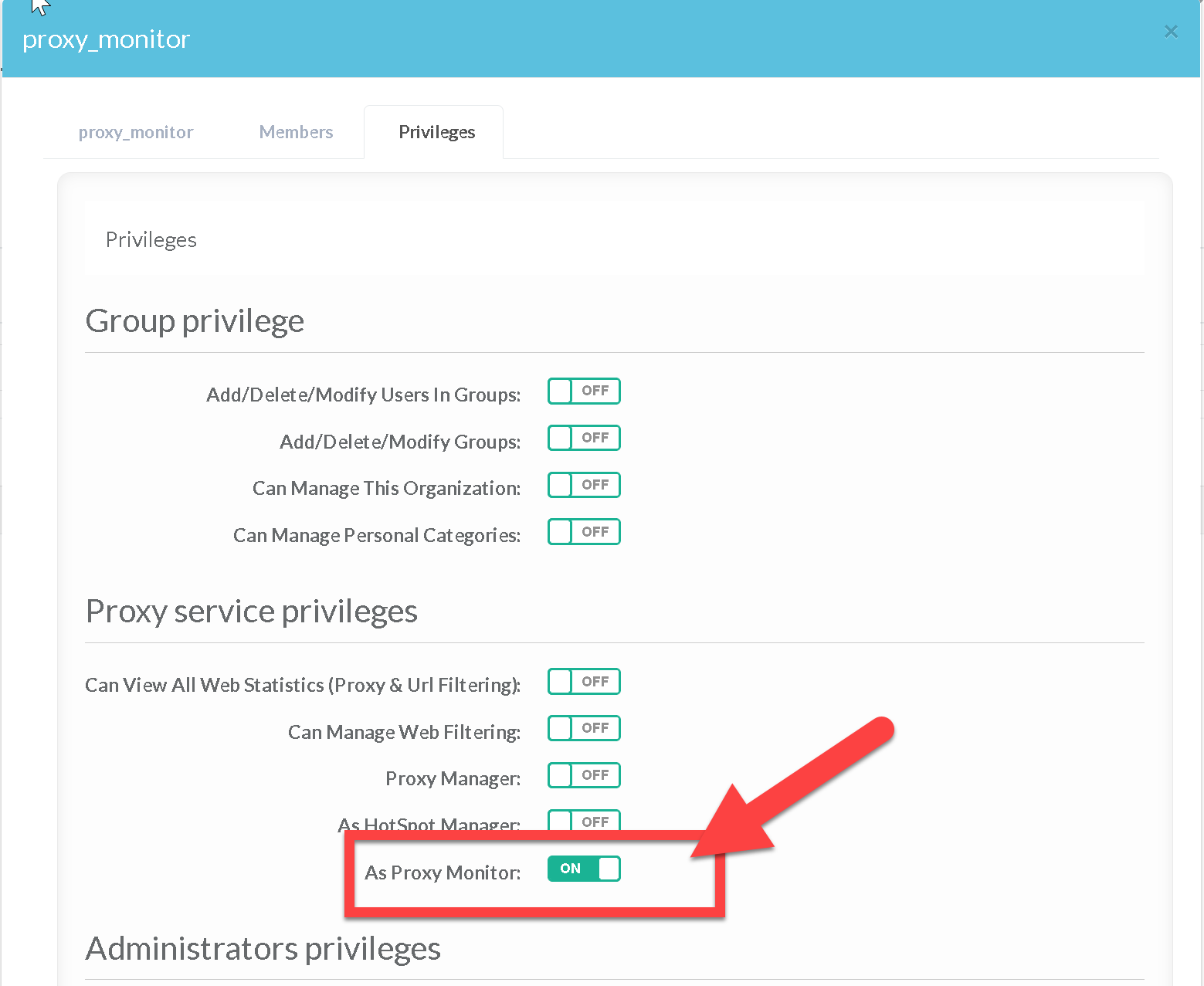
- Go into the “Privileges list” tab.
- You can see your group assigned with the “As Proxy Monitor” privilege.
¶ D) Logon as a member of the privileged group
- Now your administrator with the As Proxy Monitor privileges can be connected to the Artica Web console