As OpenSSH is widely used on a regular basis with Artica, this vulnerability may affect a large number of servers.
It is called "regreSSHion" because it has already been fixed for CVE-2006-5051 but has reappeared in more recent versions of OpenSSH.
To Fix this CVE, use the Hotfix 20240702-17
Due to the nature of this vulnerability, it would take several login attempts and several hours to exploit.
This reduces the likelihood of exploitation.
Artica users who have enabled CrowdSec can be helped by this feature
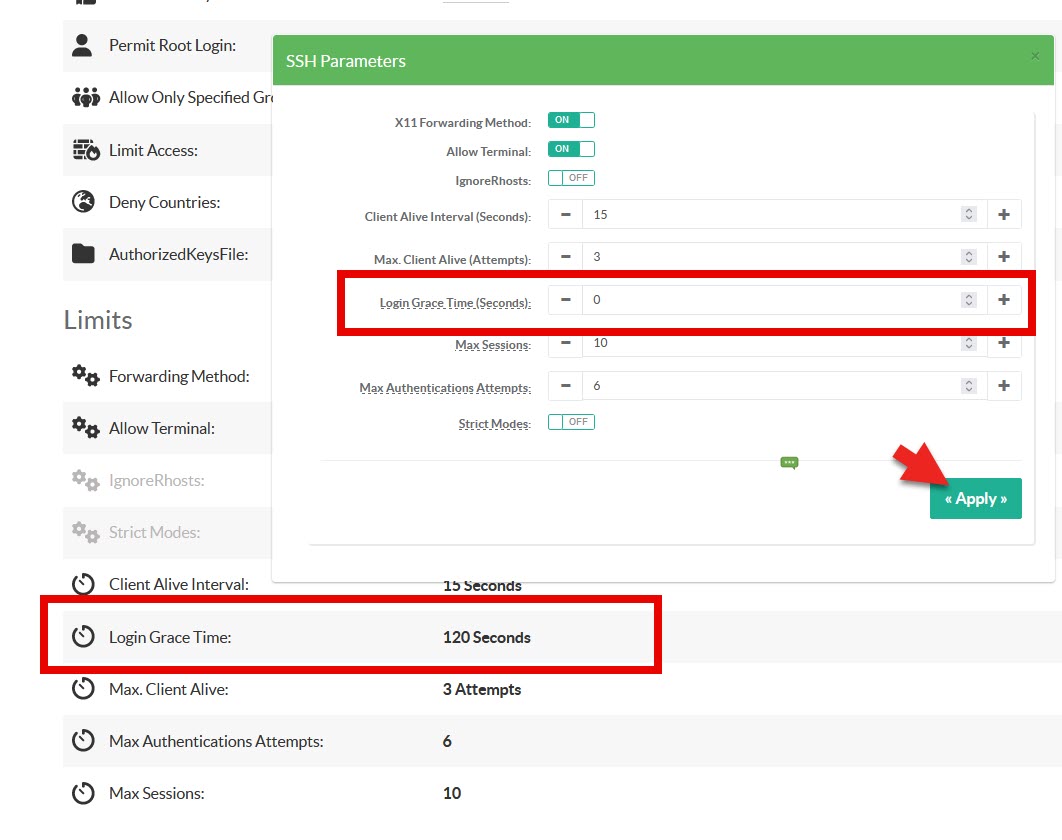
This vulnerability was discovered in the default configuration of the OpenSSH server, linked to a race condition in its signal handling.If an SSH client fails to authenticate within the Login Grace Time period (120 seconds by default), the SIGALRM handler (alarm signal) is triggered asynchronously.
However, certain functions called by this handler, such as syslog(), are not safe for use in asynchronous signal contexts.
syslog() can then invoke the unsafe asynchronous functions malloc() and free().
If interrupted during a call to one of these functions by code that also interacts with the heap, it can potentially lead to heap corruption.
This could then be exploited to manipulate the heap in order to execute arbitrary code with root privileges on the OpenSSH service process.
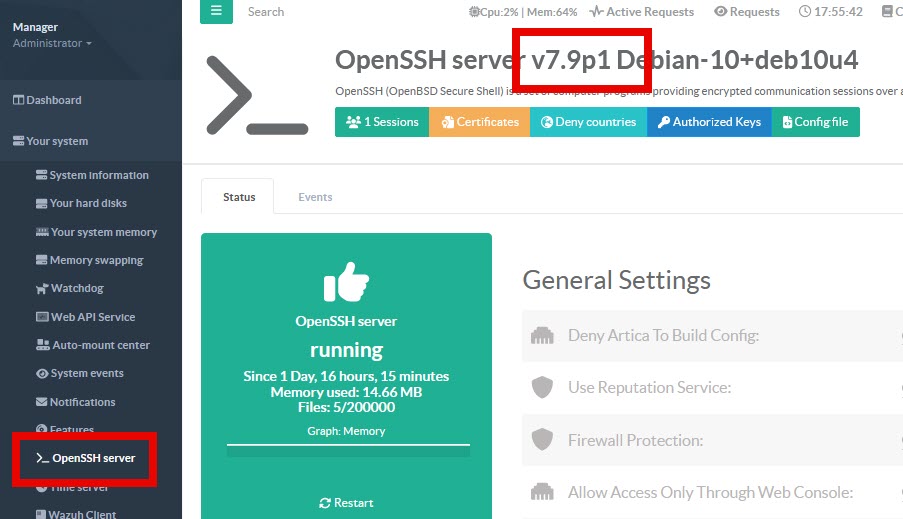
On your Artica server, check the version of your OpenSSH server inside Your System > OpenSSH server
Impacted versions are: OpenSSH versions 8.5p1 to 9.7p1 and OpenSSH versions prior to version 4.4p1
If your version is impacted, as a possible mitigation, set Login Grace Time to 0 in the configuration.
This exposes the device to denial of service but prevents the Remote Command Execution.
The Hotfix 20240702-17 allows you to set a Login Grace Time to 0 as old version return back to 120s if you set the value to 0