Services that are running and bound to the loopback interface on the Artica Proxy are accessible through the proxy service.
In particular, the "tailon" service is running, running as the root user, is bound to the loopback interface, and is listening on TCP port 7050.
Security issues associated with exposing this network service are documented at gvalkov's 'tailon' GitHub repo.
Using the tailon service, the contents of any file on the Artica Proxy can be viewed.This CVE is fixed on Artica v4.50 Service Pack 1 or Artica 4.50 Hotfix 20240309-01
The CVE-2024-2056 details can be seen here
¶ Without the Hotfix:
- The security hole can be fixed by removing the tailon feature.
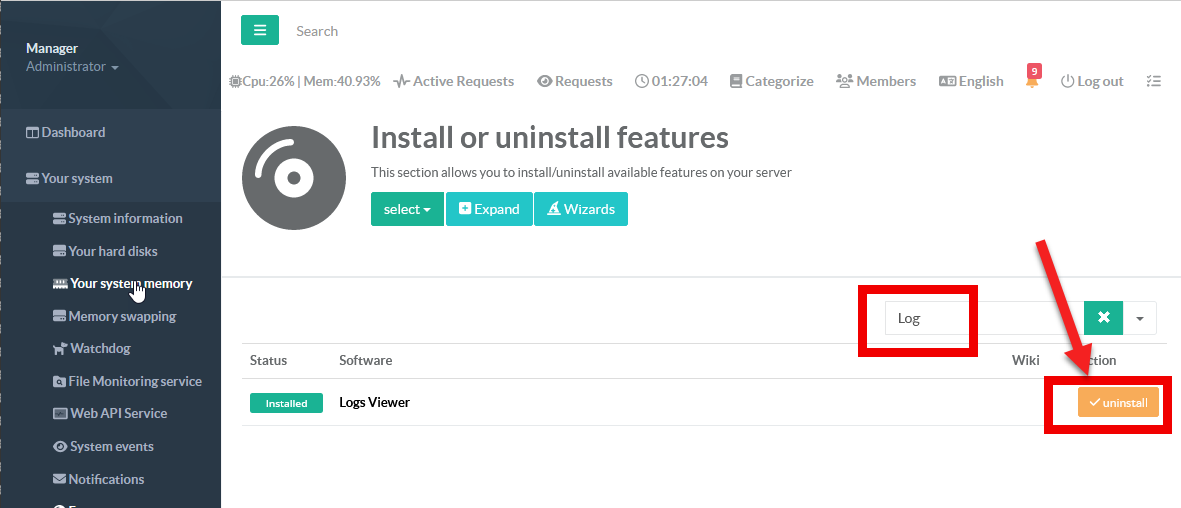
- On the left menu, choose
Your System > Features.
In the search field, typeLogand click on “Uninstall” button on “Logs Viewer” row
¶ HotFix 20240309-01 or Service Pack 1
These fixes are able to deny any request from the proxy accessing on services running on the loopback Interface.
Artica is able to detect if the rule has been added. If not, a notification in the bell informs you that Artica proxy is vulnerable.
The Fix it button takes you back to this article.
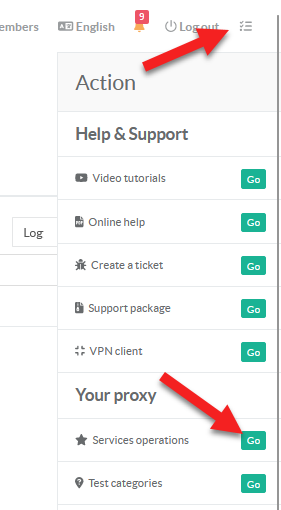
- On the right menu, choose
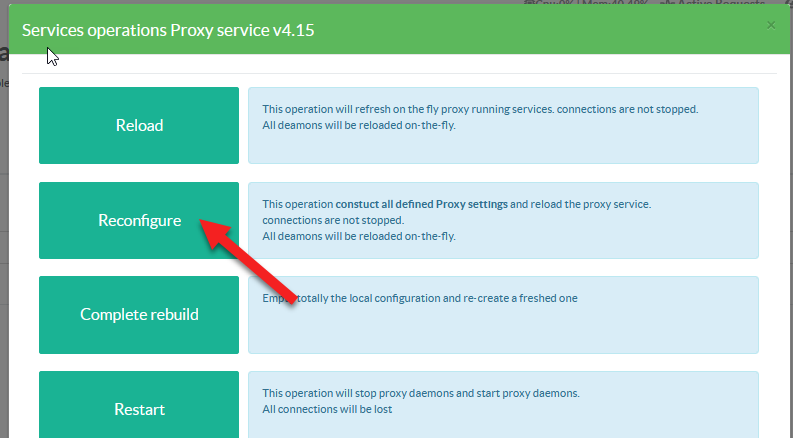
Your proxy > Service Operations.
- Choose Reconfigure