Back to Secure the Artica Web console
Reducing to a minimum the lifetime of the session tokens decreases the likelihood of a successful session hijacking attack.
This can be a control against preventing other attacks like Cross Site Scripting and Cross Site Request Forgery.
Such attacks have been known to rely on a user having an authenticated session present.
Not having a secure session termination only increases the attack surface for any of these attacks.
By default Artica use a unlimited session.
It let the user to terminate the session manually using the top right icon.
¶ Session Timeout.
The session Timeout can be set as “System Administrator” or “Manager”.
In this case, the feature is locked using accounts with less privileges.
- On the Web console, select Your system / Web Console.
- Select the desired Max session life time in the dropdown list
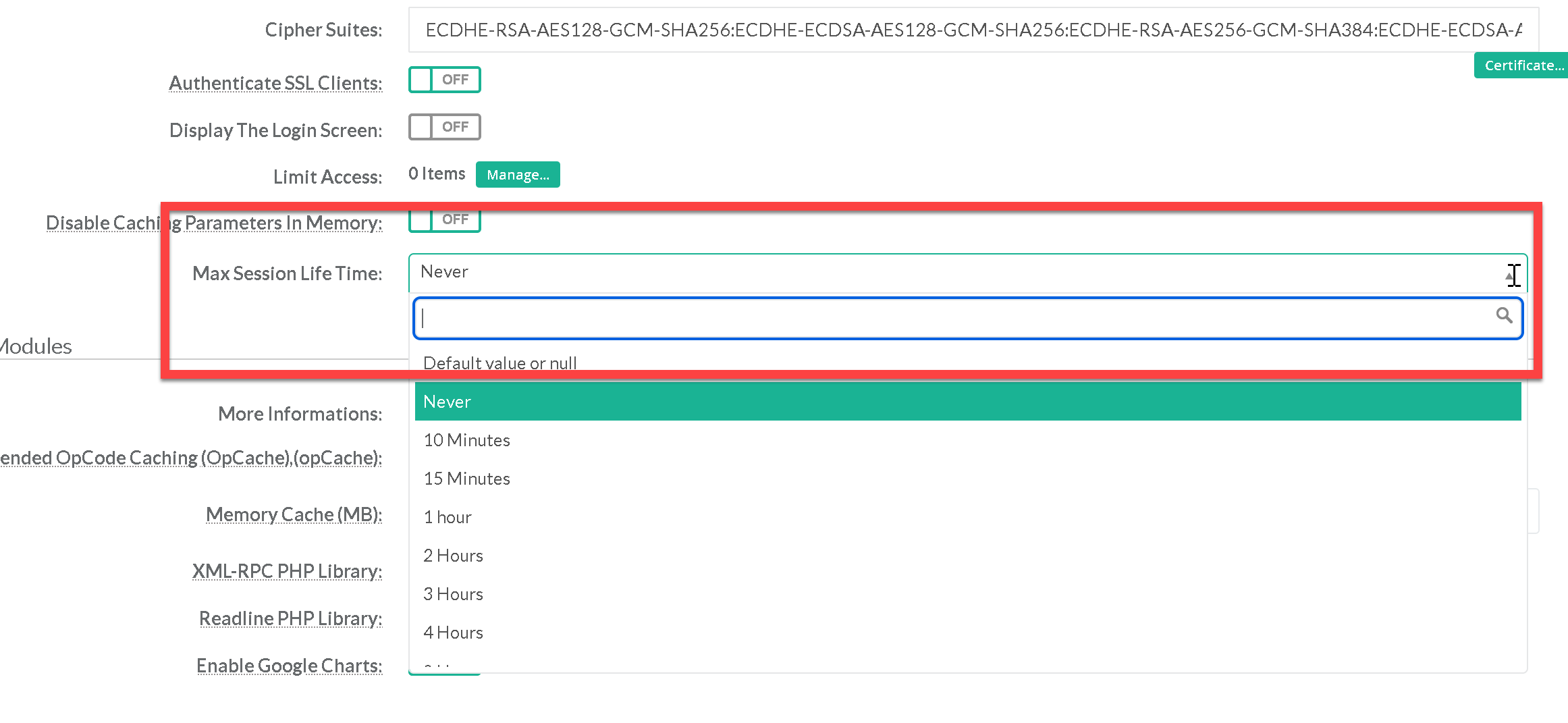
- Click on Apply button
¶ New feature on Unstable Service Pack 887 or Artica v4.40
The session timeout depends on the browser activity.
Browser activity and the regular display of widgets may result in constant browser activity.
Thus, the session is always being requested and is continually being updated.
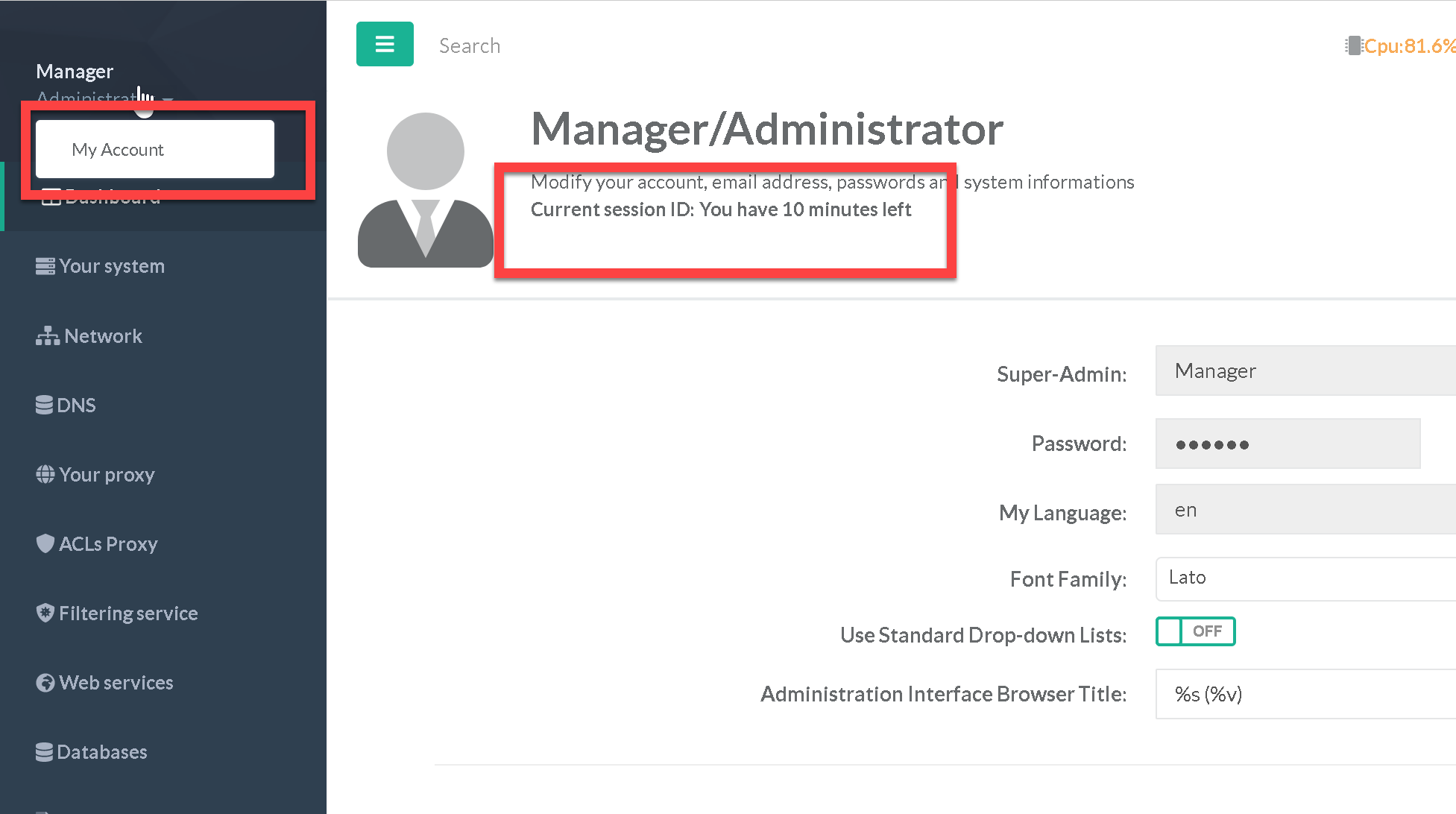
The new versions of Artica calculate a strict runtime from the login in the console.
This time limit can be viewed in the account settings.