Artica’s web interface includes a comprehensive Sudo Management module, allowing administrators to:
- Define fine-grained sudo rules for individual users or groups
- Specify which commands can be run with or without a password
- Preview and validate the generated
/etc/sudoers.dsnippets before applyingAll changes are applied atomically and syntax-checked via
visudo, ensuring secure, error-free delegation of elevated privileges.
¶ sudo is not installed by default.
The sudo package isn’t installed by default on the virtual appliances or when installing Artica from the ISO. To add it, install via apt-get:
apt-get install sudo
After you install the sudo package, Artica will automatically detect it and enable sudo-privilege management in the System User section.
¶ Groups and/or users rules
Sudo privileges can be assigned both at the group level and on a per-user basis.
In this guide, we’ll cover how to define rules for groups—the same procedure applies when configuring individual users.
¶ Create sudo rules
- In the System User section, select your group and if sudo is detected by Artica, you will see a “sudo” tab
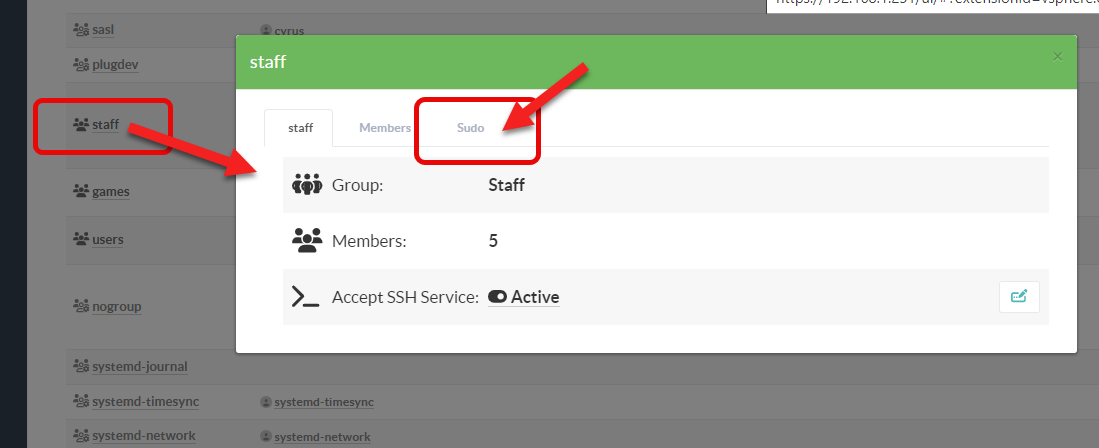
- Click on New rule button to open a new free rule
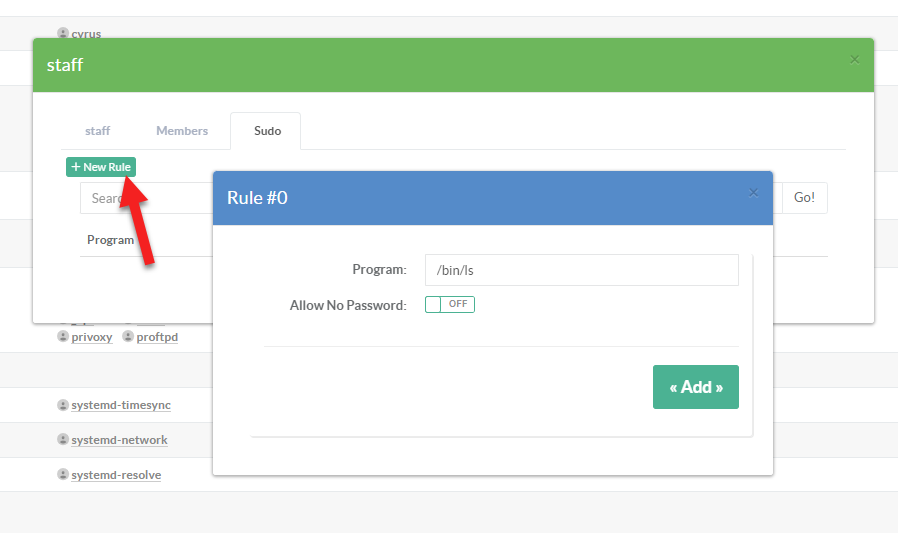
¶ The Program field
Under Program, you can specify exactly which commands are permitted to be run with sudo.
This can be the program binary itself—for example, /usr/bin/apt-get—or a specific command with its arguments, like /usr/bin/apt-get upgrade.
If you use the wildcard character *, you grant the user permission to run any command, including spawning a root shell with sudo -s.
¶ The Allow no Password
This toggle controls whether sudo prompts for the user’s password:
- Enabled : Commands run under
sudo(e.g./usr/bin/apt-get) execute as root without any password prompt. - Disabled (default):
sudo /usr/bin/apt-get(or any other allowed command) requires the invoking user to authenticate by entering their own password.