Securing your SSH service is crucial to prevent unauthorized access and potential cyber threats. Here are some essential tips to enhance SSH security on your server:
Configuration can be found in Your System > OpenSSH server
|
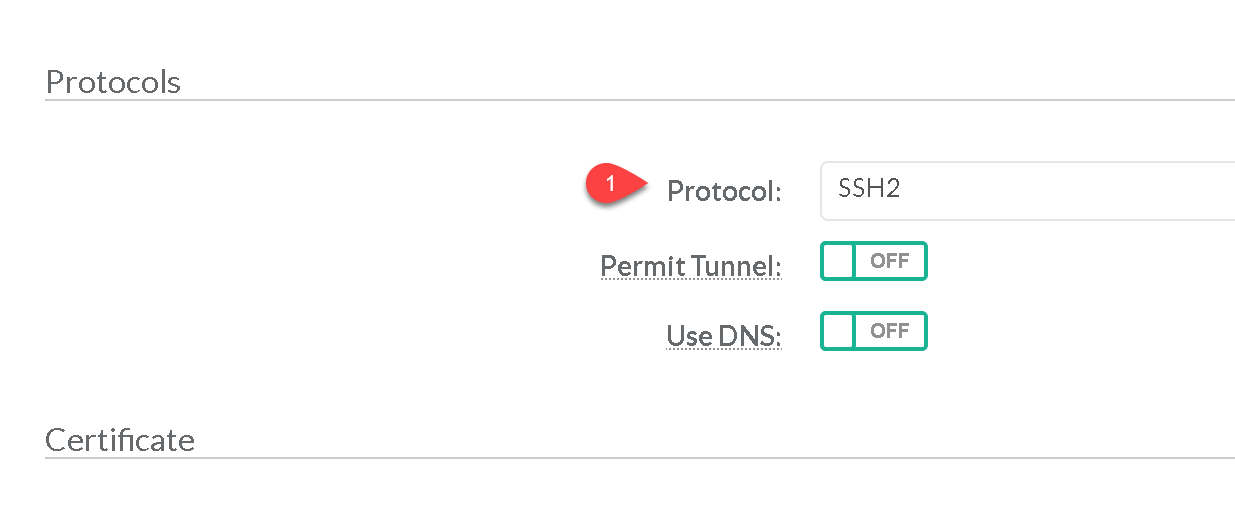
Use SSL2 protocol:
|
 |
|
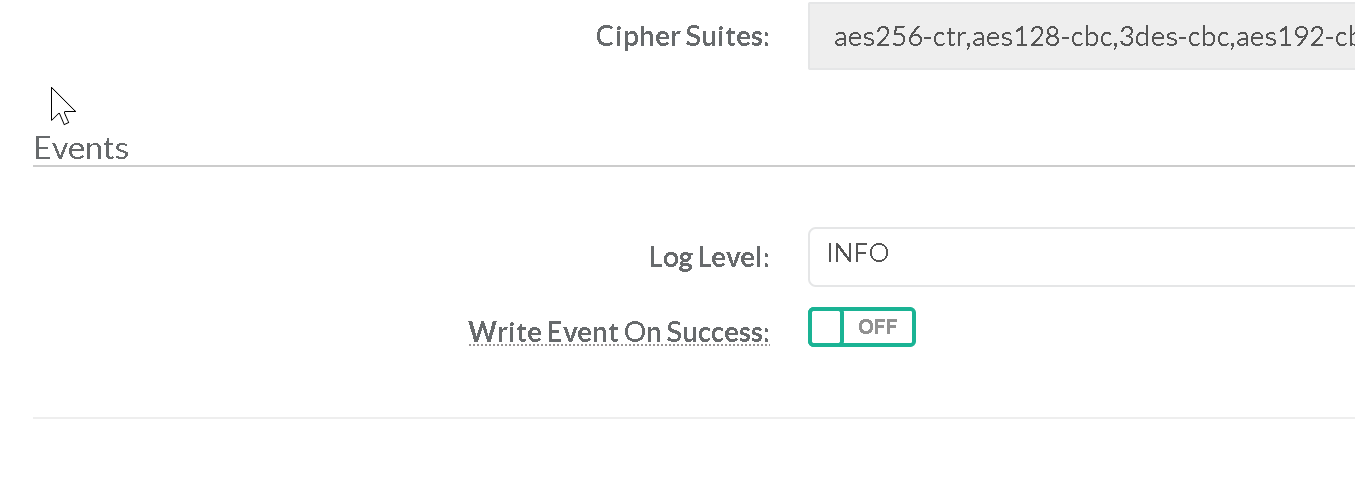
INFO level is the basic level that only records login activity of SSH users.
|
 |
|
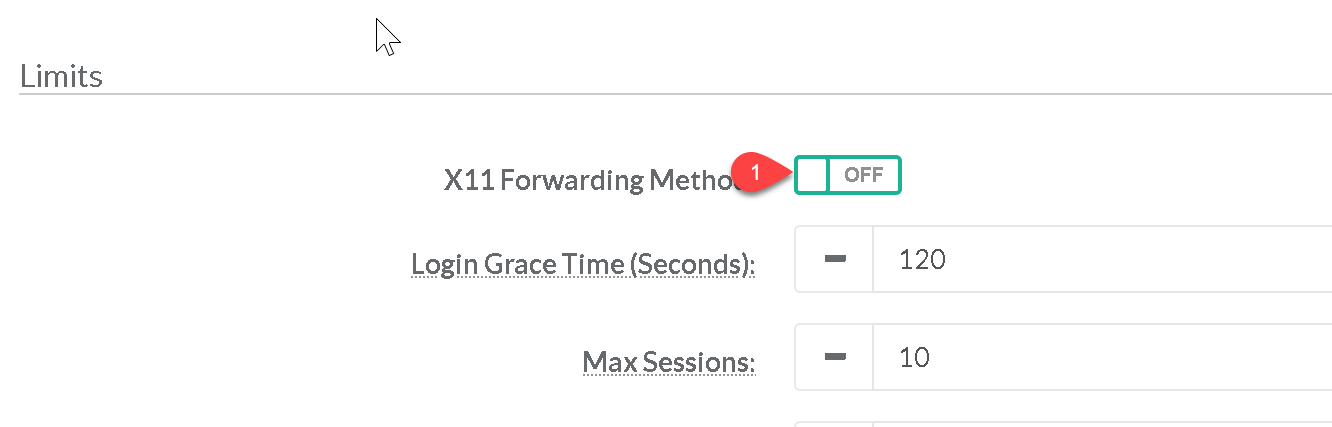
Disable X11 forwarding unless there is an operational requirement to use X11 applications directly. Set X11 Forwarding method to OFF
|
 |
|
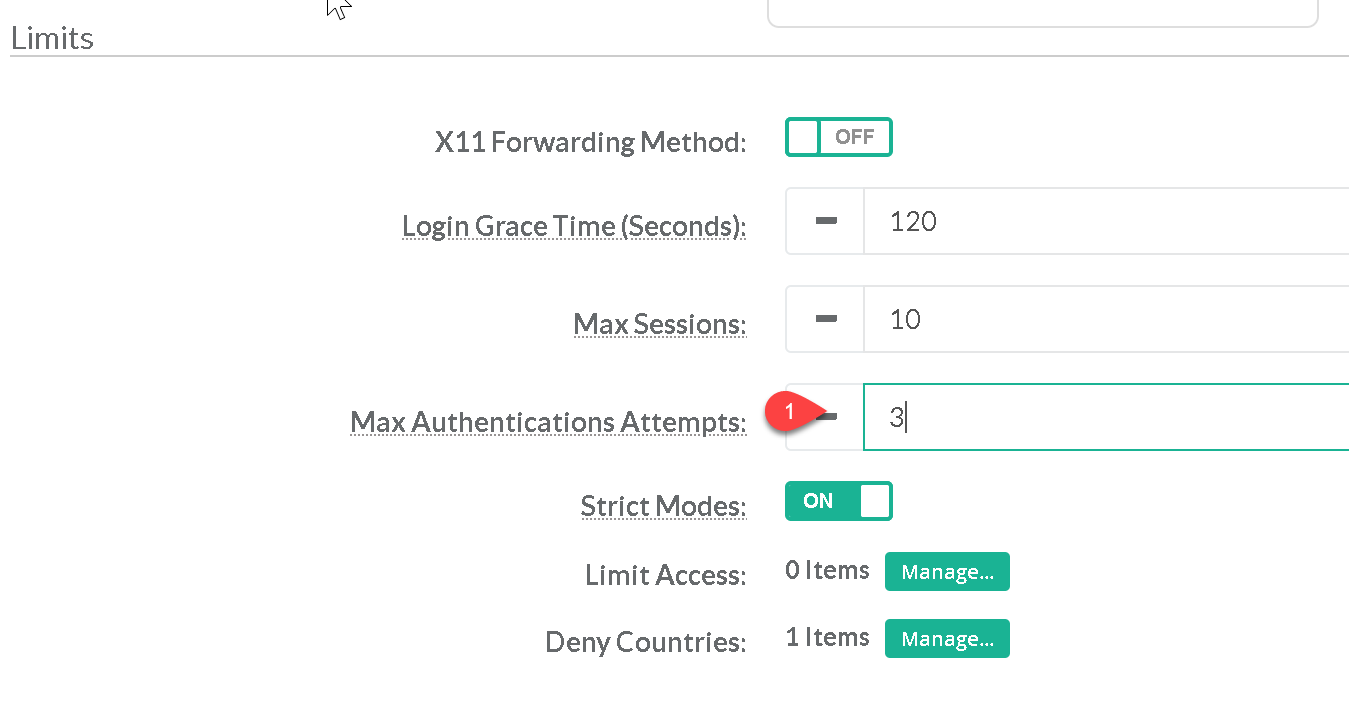
The Max authentications attempts parameter specifies the maximum number of authentication attempts permitted per connection. When the login failure count reaches half the number; error messages will be written to the syslog file detailing the login failure. Setting the Max authentications attempts parameter to a low number will minimize the risk of successful brute force attacks to the SSH server. |
 |
|
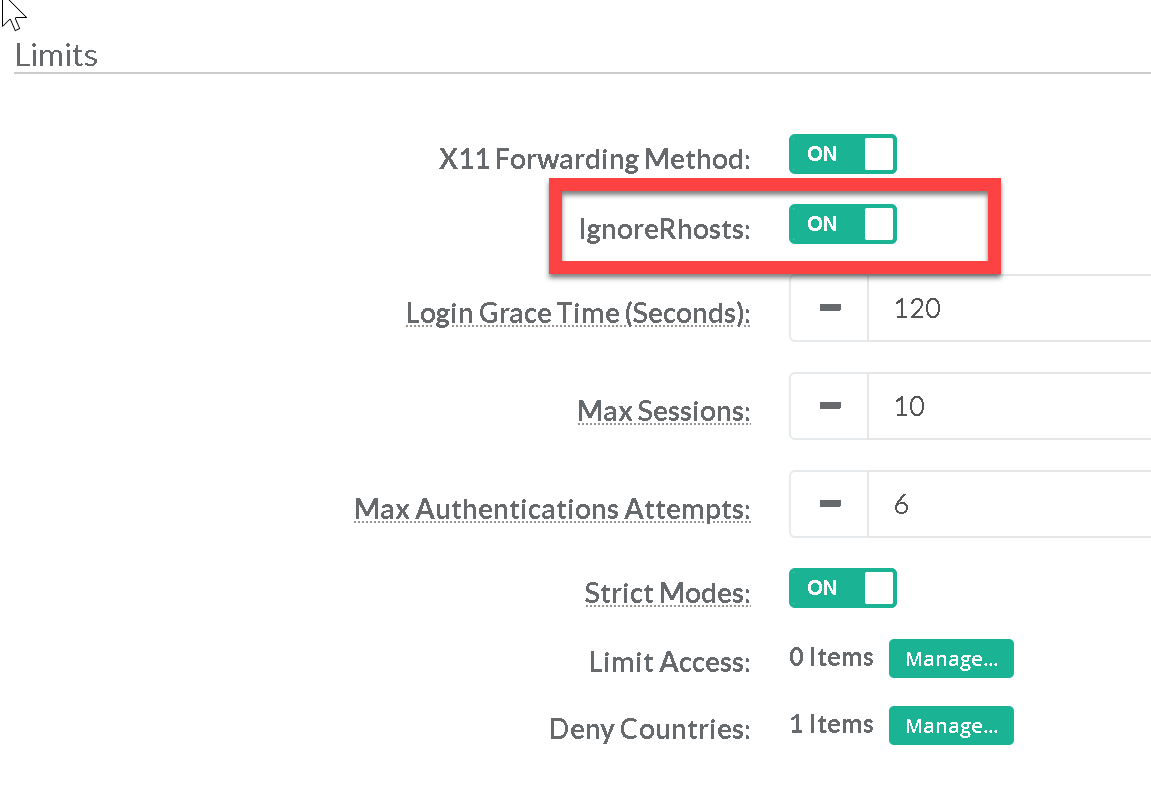
Setting IgnoreRhosts parameter forces users to enter a password when authenticating with ssh.
|
 |
|
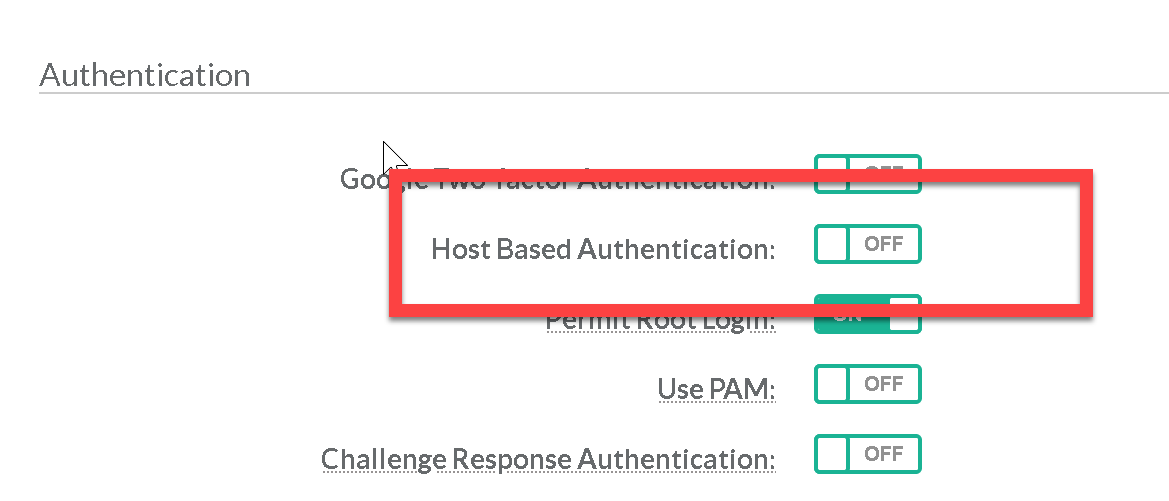
The Host based Authentication parameter specifies if authentication is allowed through trusted hosts via the user of .rhosts; or /etc/hosts.equiv; along with successful public key client host authentication. Ensure Host based Authentication is disabled
|
 |
|
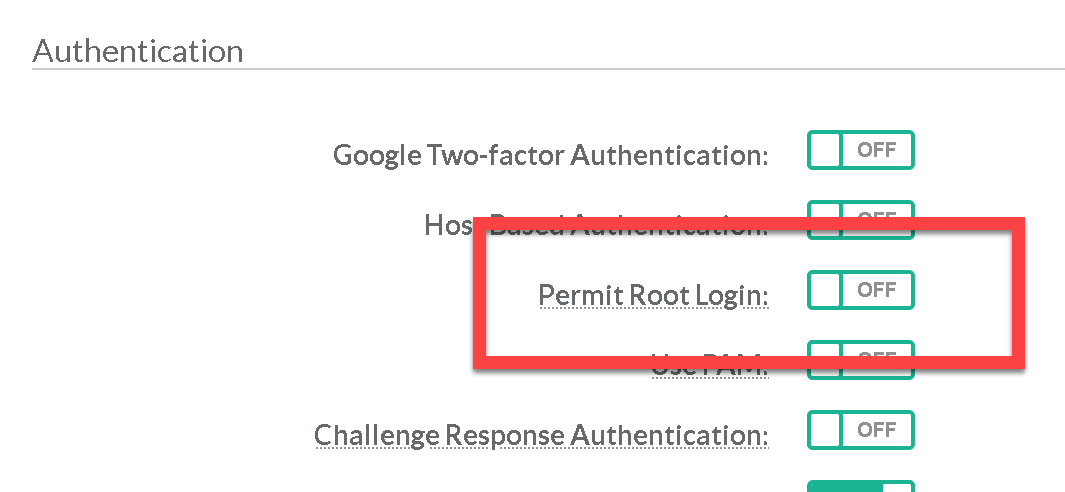
The Permit Root Login parameter specifies if the root user can log in using ssh.
|
 |
|
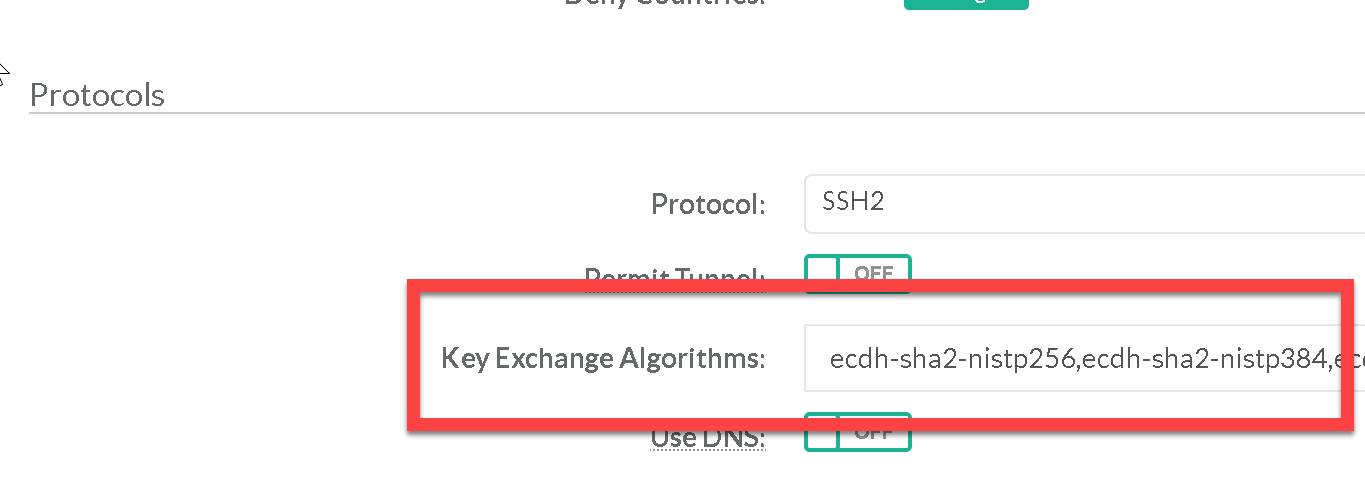
Key exchange is any method in cryptography by which cryptographic keys are exchanged between two parties; allowing use of a cryptographic algorithm. If the sender and receiver wish to exchange encrypted messages; each must be equipped to encrypt messages to be sent and decrypt messages received Ensure only strong Key Exchange algorithms are used like diffie-hellman-group1-sha1, diffie-hellman-group14-sha1, diffie-hellman-group-exchange-sha1
|
 |
|
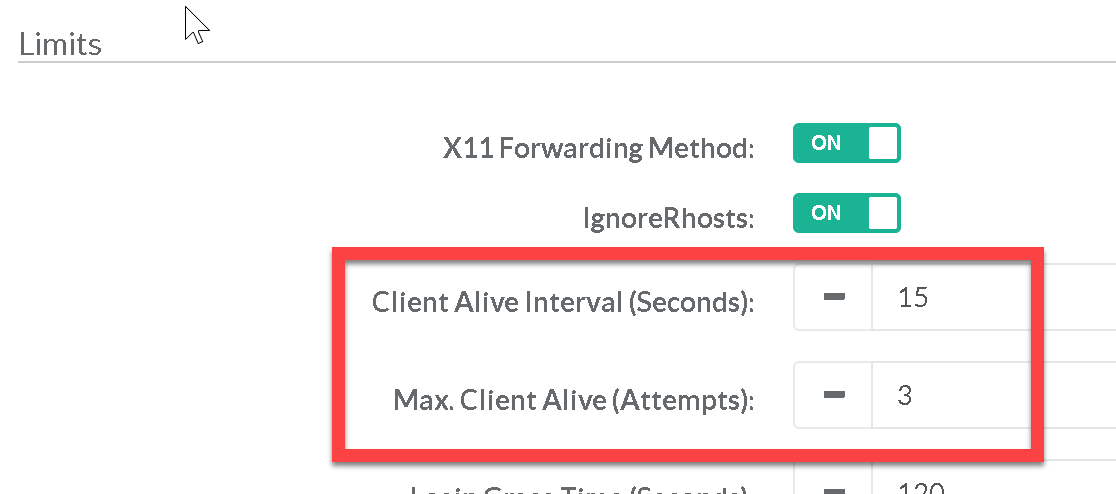
The two options Client Alive Interval and Client Alive Count Max control the timeout of ssh sessions. Having no timeout value associated with a connection could allow an unauthorized user access to another user's ssh session (e.g. user walks away from their computer and doesn't lock the screen). |
 |
|
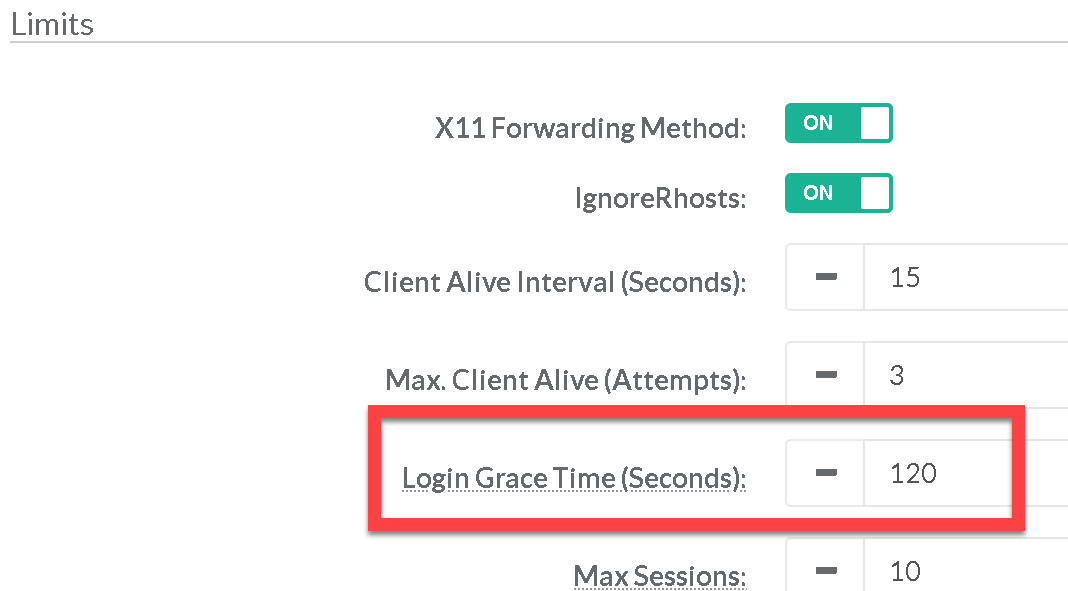
The Login Grace Time parameter specifies the time allowed for successful authentication to the SSH server. Like other session controls in this session the Grace Period should be limited to appropriate organizational limits to ensure the service is available for needed access. Ensure the Login Grace Time is set to one minute or less
|
 |
|
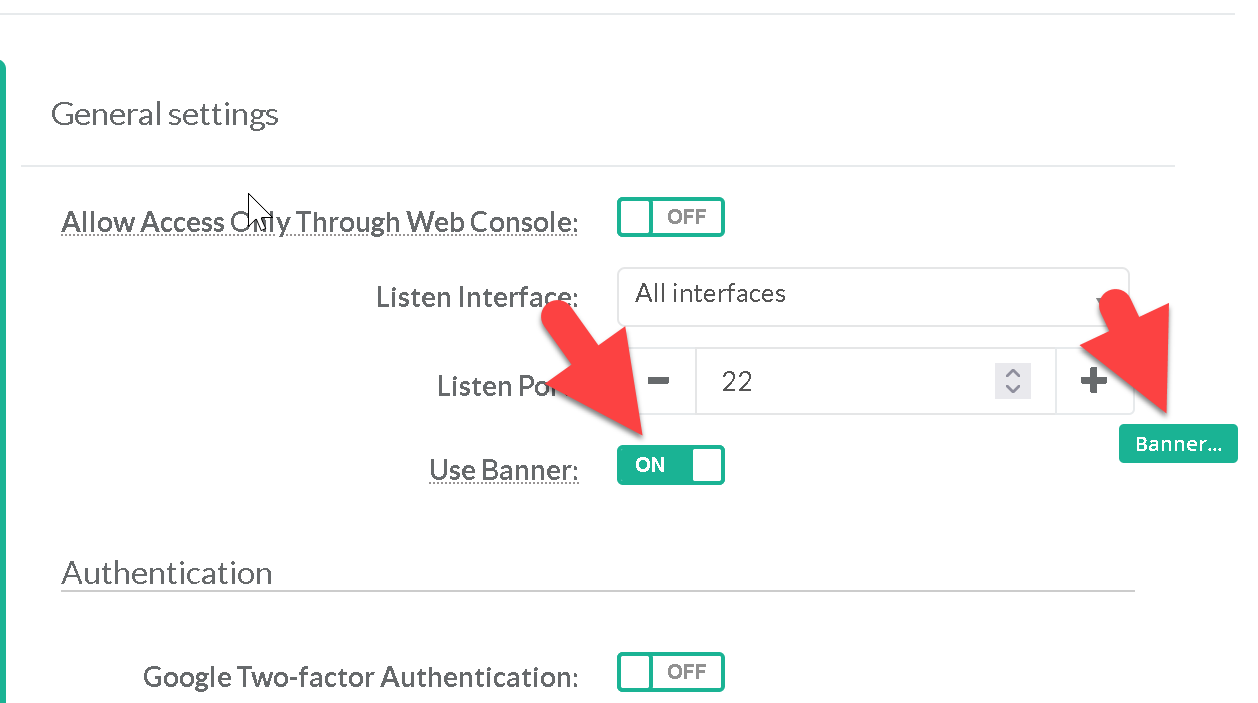
The Banner parameter specifies a file whose contents must be sent to the remote user before authentication is permitted. Presenting a warning message prior to the normal user login may assist the prosecution of trespassers on the computer system. Ensure Using banner is configured
|
 |
|
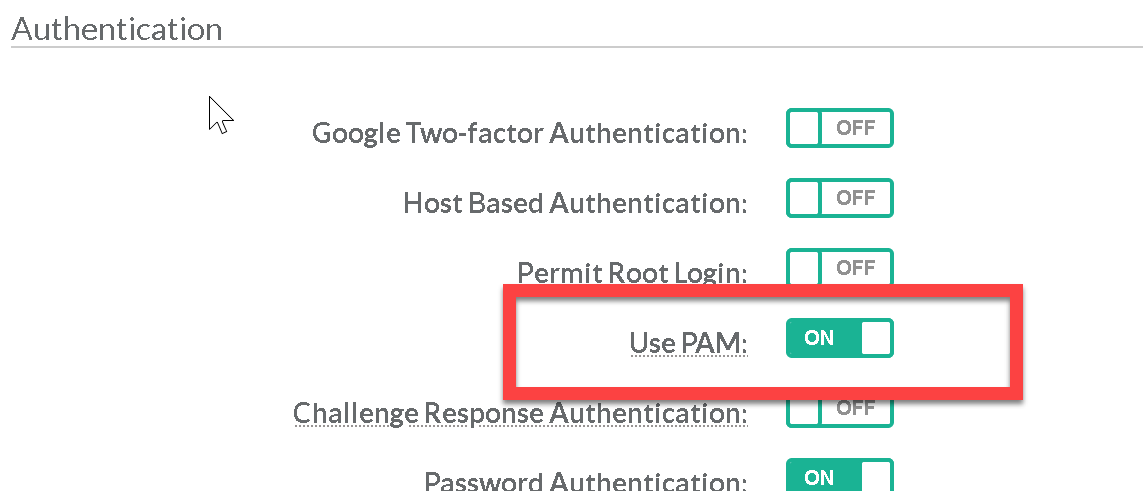
Use PAM Enables the Pluggable Authentication Module interface. When use PAM is active; PAM runs through account and session types properly. |
 |
|
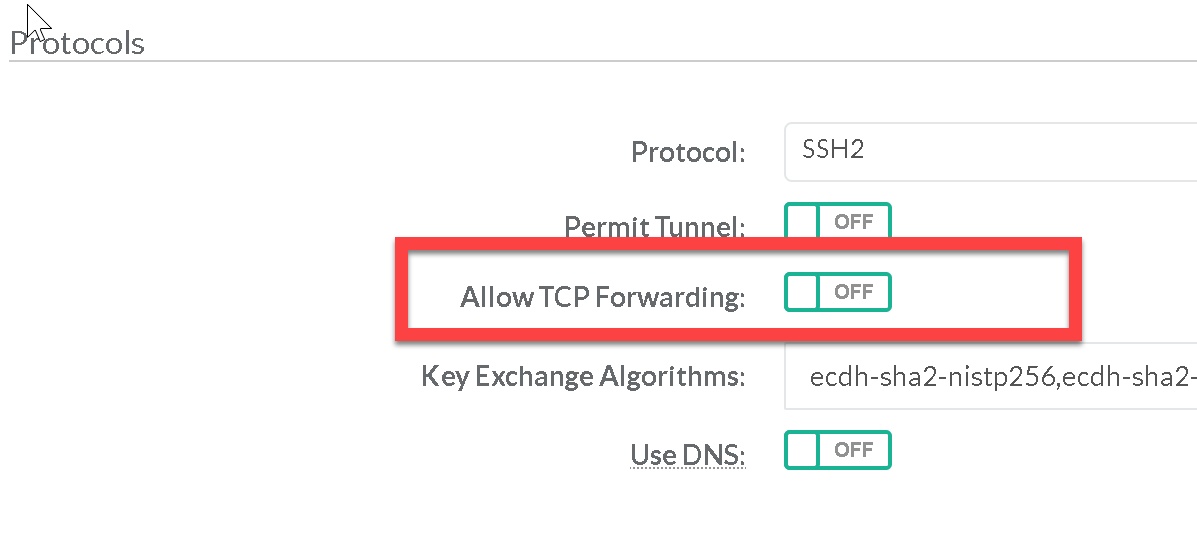
SSH port forwarding is a mechanism in SSH for tunneling application ports from the client to the server; or servers to clients. It can be used for adding encryption to legacy applications; going through firewalls; and some system administrators and IT professionals use it for opening backdoors into the internal network from their home machines. Leaving port forwarding enabled can expose the organization to security risks and back-doors. Ensure Allow TCP Forwarding is set to OFF |
 |
|
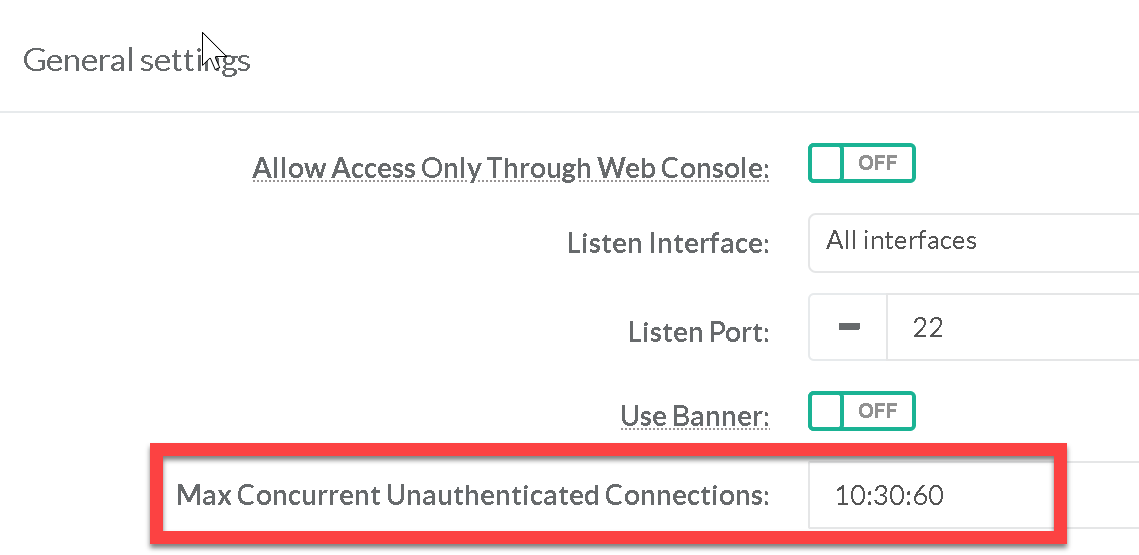
The Max concurrent unauthenticated connections parameter specifies the maximum number of concurrent unauthenticated connections to the SSH daemon. To protect a system from denial of service due to a large number of pending authentication connection attempts; use the rate limiting function of Max concurrent unauthenticated connections to protect availability of sshd logins and prevent overwhelming the daemon. Ensure SSH Max concurrent unauthenticated connections is limited |
 |
|
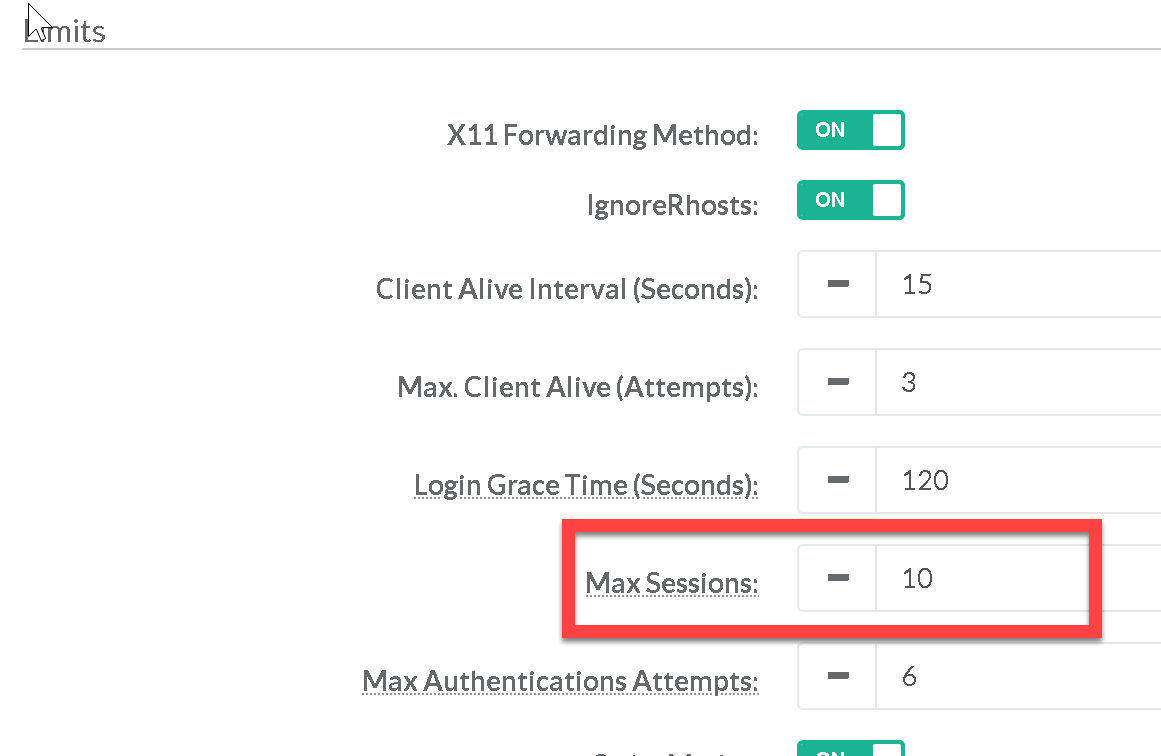
The Max Sessions parameter specifies the maximum number of open sessions permitted from a given connection. To protect a system from denial of service due to a large number of concurrent sessions; use the rate limiting function of Max Sessions to protect availability of sshd logins and prevent overwhelming the daemon. |
 |