Proxy ACLs are similar to firewall rules.
It is the same operating principle but only applies to the SMTP protocol
¶ An SMTP rule
An SMTP rule has its own action on a message (like a firewall).
When you create a firewall rule, it allows you to authorize, prohibit, mark network packets, transfer packets to another gateway, etc.
SMTP rules allow you to define specific operations on messages:
- Allow connections:
Accept the message, this is designed to white-list the message against next rules.
- Discard
Claim successful delivery and silently discard the message.
Log the optional text if specified, otherwise log a generic message
- Blind carbon copy
Send one copy of the message to the specified recipient.
- Information
Optional text... Log an "info:" record with the optional text... (or log a generic text), and inspect the next input line.
This action is useful for routine logging or for debugging.
- Reject.
Reject the entire message.
Reply with optional text... when the optional text is specified, otherwise reply with a generic error message.
- Prepend:
Prepend one line with the specified text, and inspect the next input line
- Backup messages:
Stores messages in the PostGreSQL table for searching, downloading and resending.
- Sign the message using the DKIM method.
(Under construction, available end of September )
Rules that modify message content do not stop the rule reading process.
The Blind carbon copy, Information and Prepend rules, for example, will effectively modify the messages, but the filter will continue to process the rules until a rule tells it to stop processing the ruleset.However, at the end, by default, the messages are forwarded to the message transfer process
Let's say we want to modify the subject of a certain type of message, the message will pass through the Prepend rule.
If this rule is followed by an "Allow connections" rule, then the message will be modified and transmitted without the other rules being processed.
¶ An SMTP object
¶ Object definition
An SMTP object is a container or group that stores records related to its detection type.
You can add as many objects as you like to the rule.
When you add objects to a rule, the relationship will be an AND.
This means, for example, that if you add two objects, for the rule to match, the message must correspond to at least one record that is part of both objects.
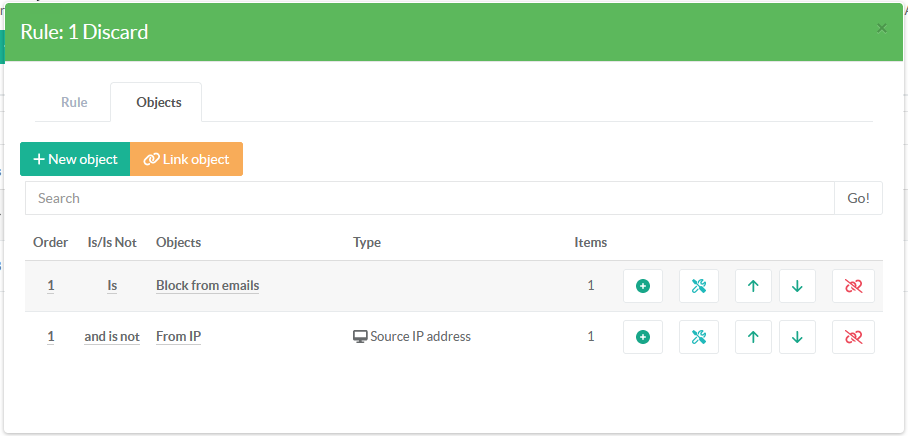
In the example below, a message will be silently rejected if and only if the message corresponds to one of the records belonging to the two objects "Block from emails" and "From IP".

¶ Negative matches
The notion of negation exists in an object that is linked to a rule, meaning that if a negation is activated on the object then the message will match if no match has been found in the object's records.
In the following example, the message will only be rejected if it matches the records stored by "Block from emails" and no records stored by "From IP" match.