The website uses arguments in the URL to determine the number of elements to display.
But malicious Internet users use this argument to overload the server by setting the value to 9999.
for example, we have this kind of query
/us/articles-cc?from-xhr&resultsPerPage=99999&_=77639142094571
As you can see, the resultsPerPage parameter is used to force the website to calculate and display 99999 elements.
To deny this kind of malicious query we can prevent the reverse-proxy from transmitting the request to the backend if the argument is greater than a value that makes sense for viewing the page ( max 200 for example )
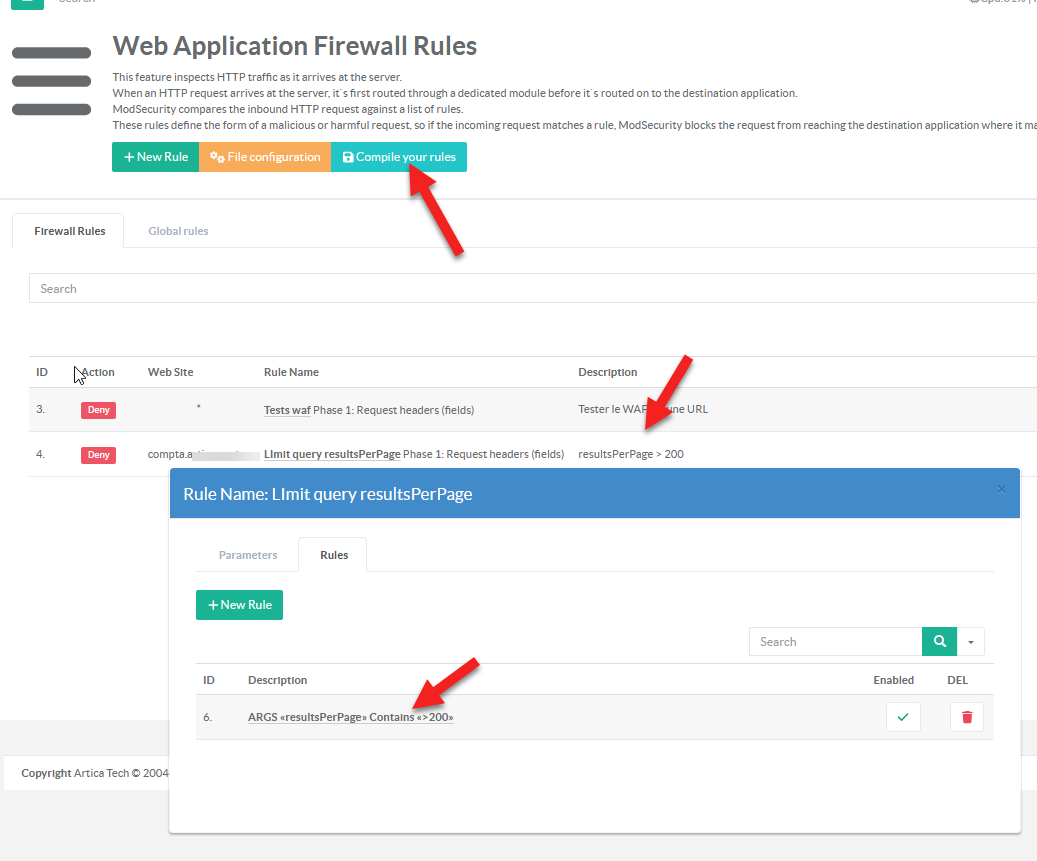
In the left menu to the Web Firewall > Rules, create a new rule that Deny accesses
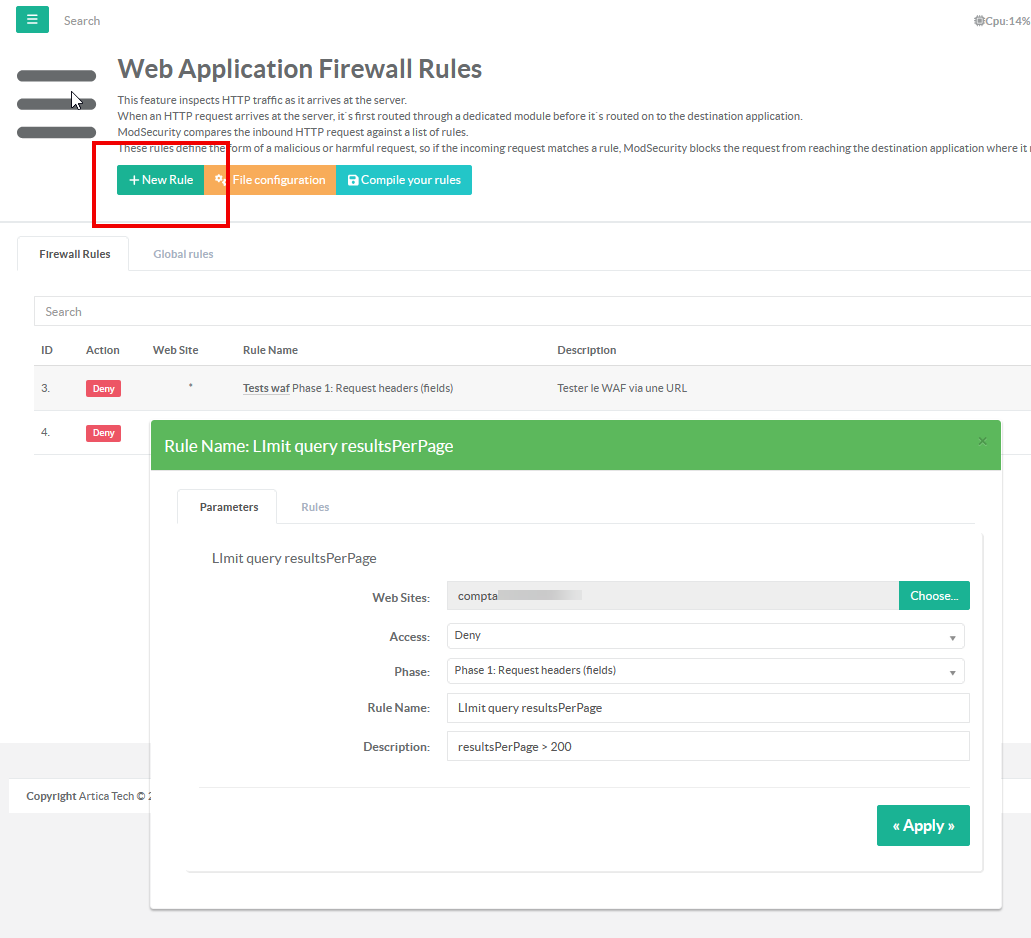
- Select Rules, and add a new Rule
- Open the new created rule
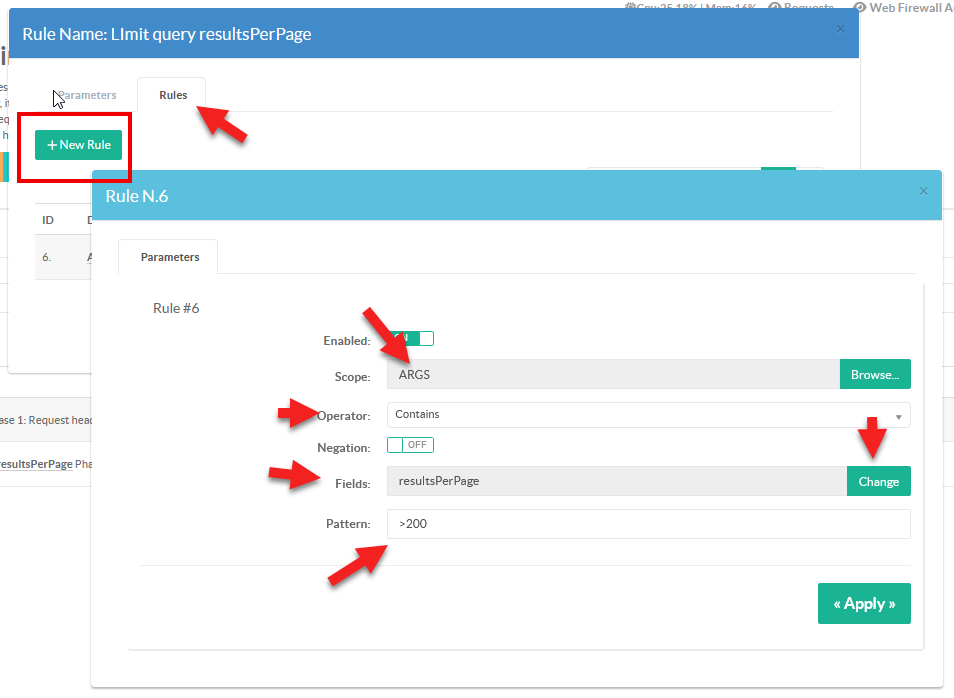
- On the Scope choose
ARGS - On the Operator, choose “
Contains” - Click on the Change button and add the argument ( in our case “resultsPerPage” - case sensitive )
- On the Pattern, set the operator (
> < =are supported ) and the desired value to check the operator in our case “> 200” - Click on
Compile Your ruleto make the rule in production mode