This should applies on all Artica versions and HaCluster using Kerberos method.
After trying to connect to your Active Directory server, Artica report the error :
KDC has no support for encryption type while getting credentials
Microsoft has described the issue in “Unsupported etype” error when accessing a resource in a trusted domain" document.
In Windows’ System Event Log the following entry could be found:
Log Name: SystemSource: Microsoft-Windows-Kerberos-Key-Distribution-Center Event ID: 14 Task Category: None Level: Error
While processing an AS request for target service xxxx, the account user did not have a suitable key for generating a Kerberos ticket (the missing key has an ID of 1). The requested etypes : 18 20 26 19 17 25. The accounts available etypes : 23 -133 -128. Changing or resetting the password of user will generate a proper key.
This means that there is a mismatch between the level of encryption defined by Artica and that offered by your Active Directory server.
This depends on the version of Active Directory and the Kerberos security measures you have in place for your domain.
¶ Display your supported domain encryption types.
- On your Active Directory server, run the gpmc.msc ( Group Policy Management )
- Locate the “Default Domain Controllers Policy” under the “Domain Controllers” branch
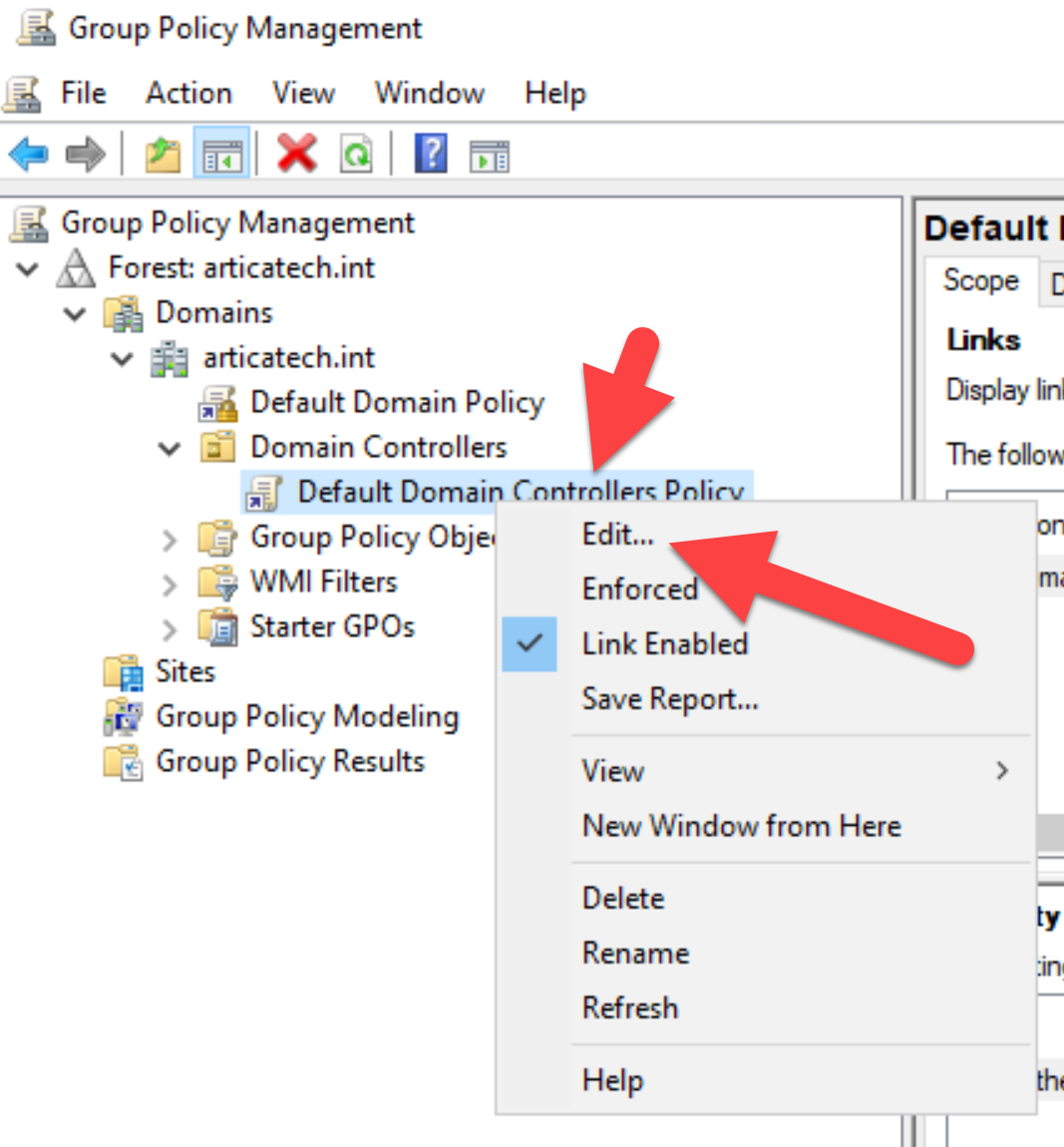
- Locate the following location:
Computer Configuration > Policies > Windows Settings > Security Settings > Local Policies > Security Options - Select the Network security: Configure encryption types allowed for Kerberos option
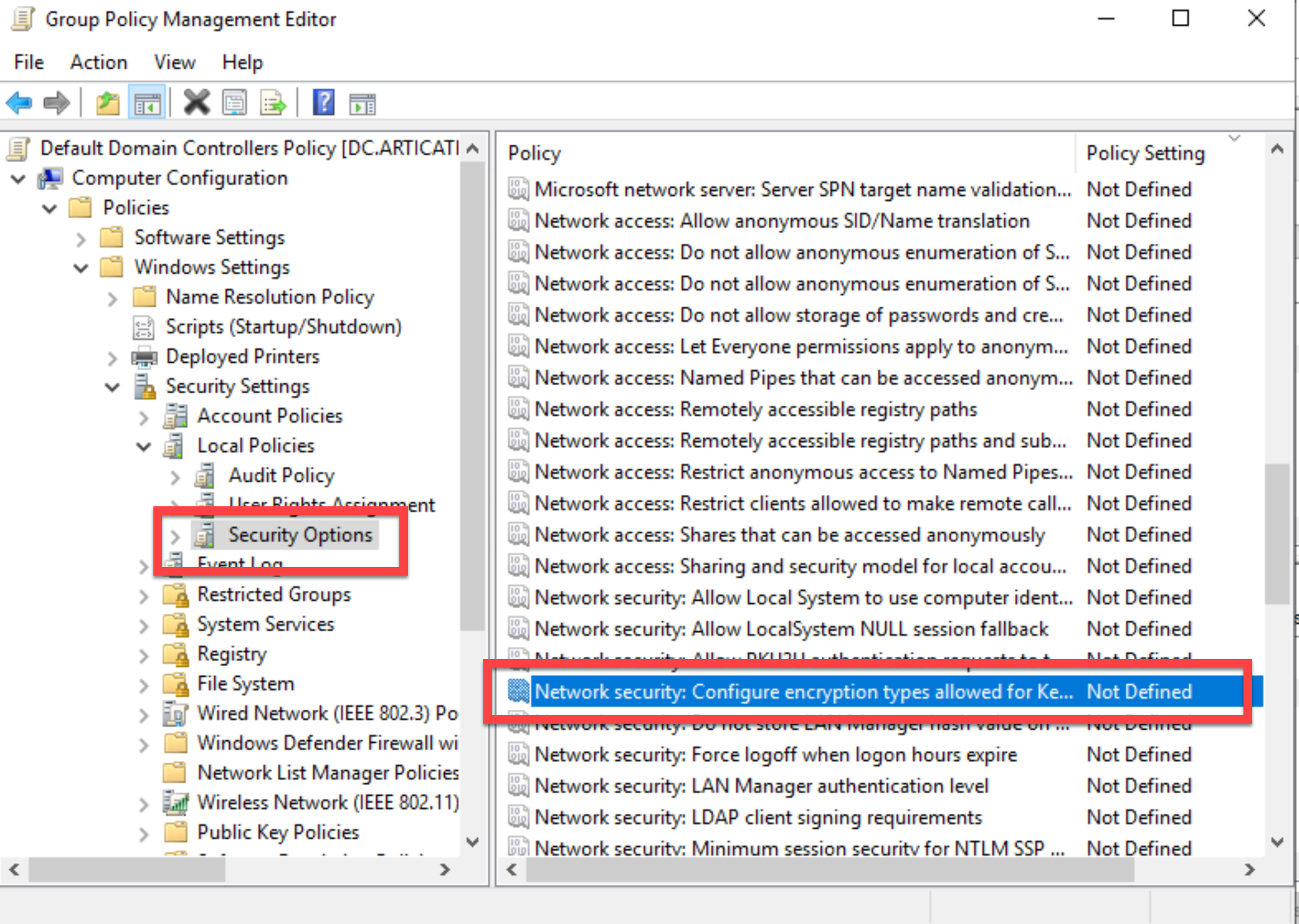
- For more information, refer to this Microsoft Article “Windows Configurations for Kerberos Supported Encryption Type”
¶ Enforce Kerberos Supported Encryption type on Artica HaCluster
Change the Kerberos Supported Encryption type on HaCluster.
On the HaCluster, the Kerberos supported Encryption type is by default “rc4-hmac des3-hmac-sha1”.
You can change it using this method.