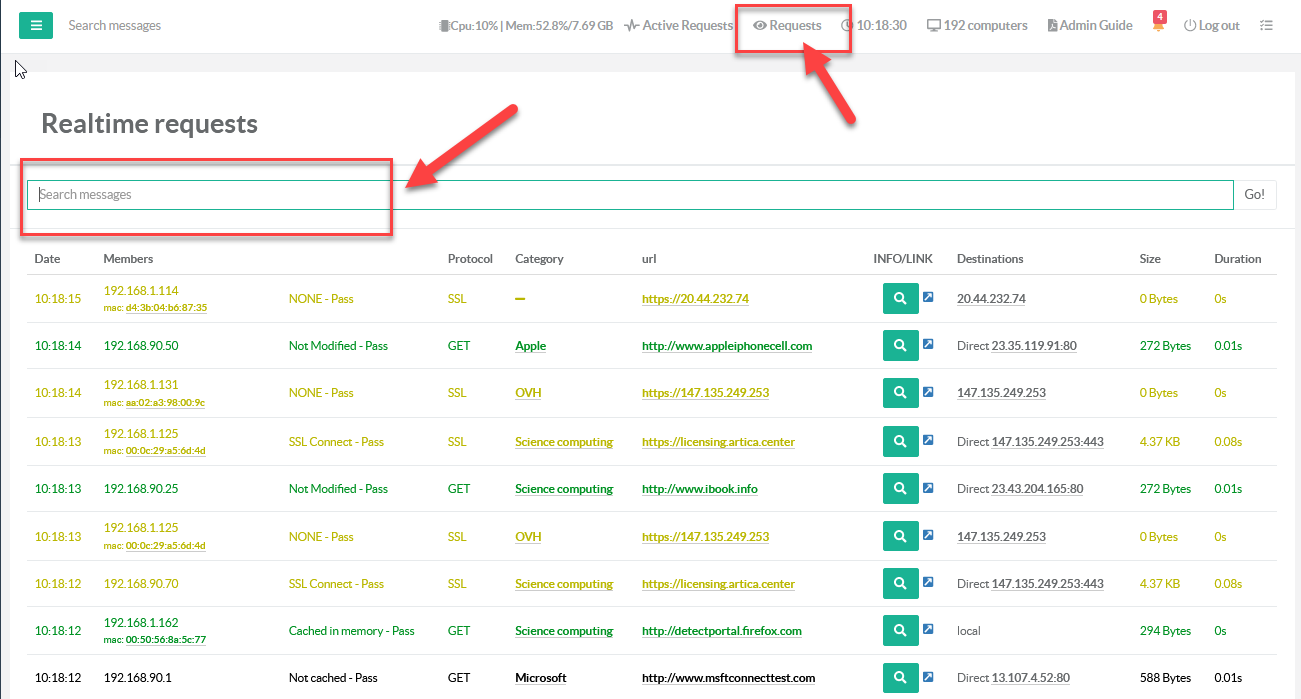
The Realtime Requests allows you to display requests by query directly proxy the legal log.
You can play with the search field to find critical events:
¶ The “events xx” word
the “events” word added with a number enforce the number of rows in the result.
If you want to search the word “google” you can set
google events 500 or 500 events google to find last 500 rows with the word “google”
¶ Regular expression
Using Regular expressions is possible : go[a-z]gle\.[a-z][a-z][a-z] 50 events
¶ Username or IP address or MAC or domain or category :
username or IP address or MAC or domain or category are “words” you can set angelique 100 events to find the word “angelique” as username in events
¶ Username and IP address and domain
If you need to use “AND” you have to use the same “word” separated by a space and start search but the terms order is mandatory.
First the IP address, second the username and finally the domain.
The search 192.168.1.32*angelique 50 events will search the IP 192.168.1.32 and the word angelique.
The search 192.168.1.32*angelique*google will search the IP 192.168.1.32 and the word angelique and the word domain.
¶ Search failed requests
To search failed requests, you can search a status code up to 200
The regular expression “\/[3-5][0-9][0-9]” will find all status codes between 300 to 599
The search \/[3-5][0-9][0-9] 50 events will find all last 50 bad requests
The search 192.168.1.32*\/[3-5][0-9][0-9]*angelique will find all bad requests requested by 192.168.1.32 with user angelique
¶ Search SSL connections
To search SSL connections, use the word “[[:space:]]CONNECT”
The query [[:space:]]CONNECT 50 events will search last 50 events on SSL connections
The query 192.168.1.32*[[:space:]]CONNECTwill search all SSL connections for 192.168.1.32 ip address
The query 192.168.1.32*[[:space:]]CONNECT*angelique will find all SSL requests from 192.168.1.32 with user angelique
The query 192.168.1.32*\/[3-5][0-9][0-9]*[[:space:]]CONNECT*angelique will find all bad ssl requests from 192.168.1.32 with user angelique