Sometimes administrators modifies the encryption types allowed for Kerberos GPO in
Computer Configuration > Policies > Windows Settings > Security Settings > Local Policies > Security Options > Network securityThis GPO may cause difficulties when generating the keytab for Artica.
The solution is to enforce the encryption level for the HTTP service account that will hold the Kerberos ticket.
- On PowerShell, run
Set-ADUser "useraccount" -Replace @{'msDS-SupportedEncryptionTypes'=24}
- Here the table of decimal values of required encryption types
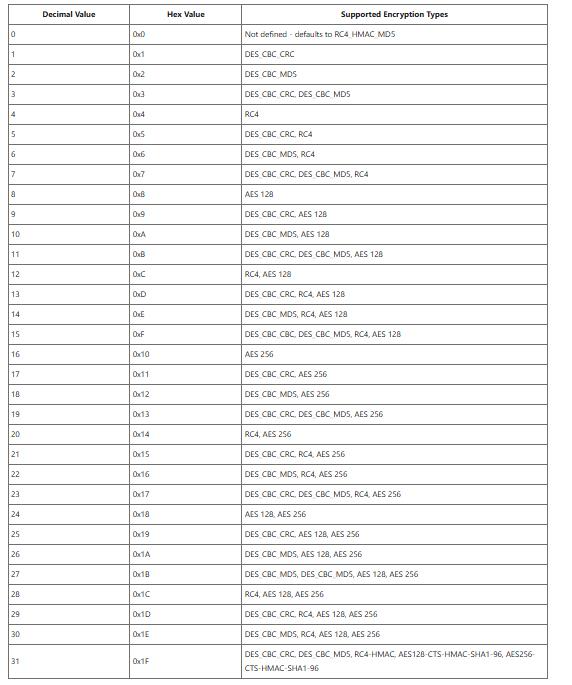
By default, the value is set to 0, so the keytab doesn’t include AES128 or AES256 keys even if you specify them in the command.
Then, you can run the standard command: ktpass -princ ...
To check the current value, use:
Get-ADUser "useraccount" -Properties msDS-SupportedEncryptionTypes | Select Name, msDS-SupportedEncryptionTypes