If you want to limit access to the user used by Artica, it must have sufficient privileges to manage Service Principal Names (SPNs) in the AD. Typically, this is done by a domain administrator or a delegated service account with SPN management rights
¶ Use PowerShell to Assign Permissions
You can grant the Read and Write permissions on the servicePrincipalName attribute using the dsacls command.
Here's how you can do it:
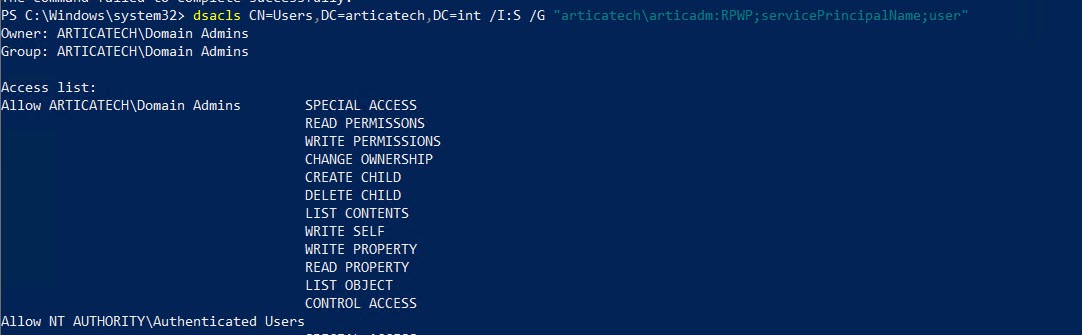
We want to add delegation to the CN=Users,DC=articatech,DC=int branch with user articatech\articadm
dsacls CN=Users,DC=articatech,DC=int /I:S /G "articatech\articadm:RPWP;servicePrincipalName;user"
¶ Determine the User Details:
Identify the Organizational Unit (OU) where the user accounts or service accounts are located, and the username of the account that will manage SPNs.
Run the PowerShell command line:
dsacls "CN=articadm,CN=Users,DC=articatech,DC=int" | findstr "SPECIAL ACCESS" | findstr "service principal name"
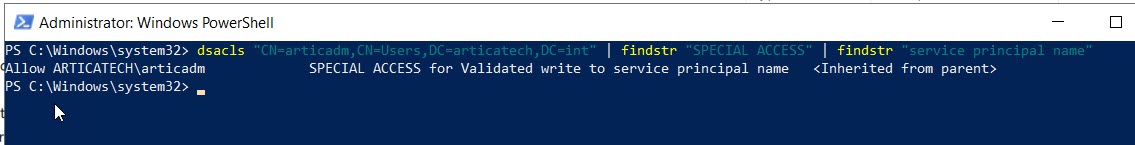
You see in the privilege in the output