Please note that this simulation does not give the exact result.
In fact, users first go through the proxy service, which also has access rules through its ACLs, its identification system...
It simply allows you to validate whether or not a user or group of users is filtered through your url filtering rules.
- Under the right menu, choose “Verify rules” option.
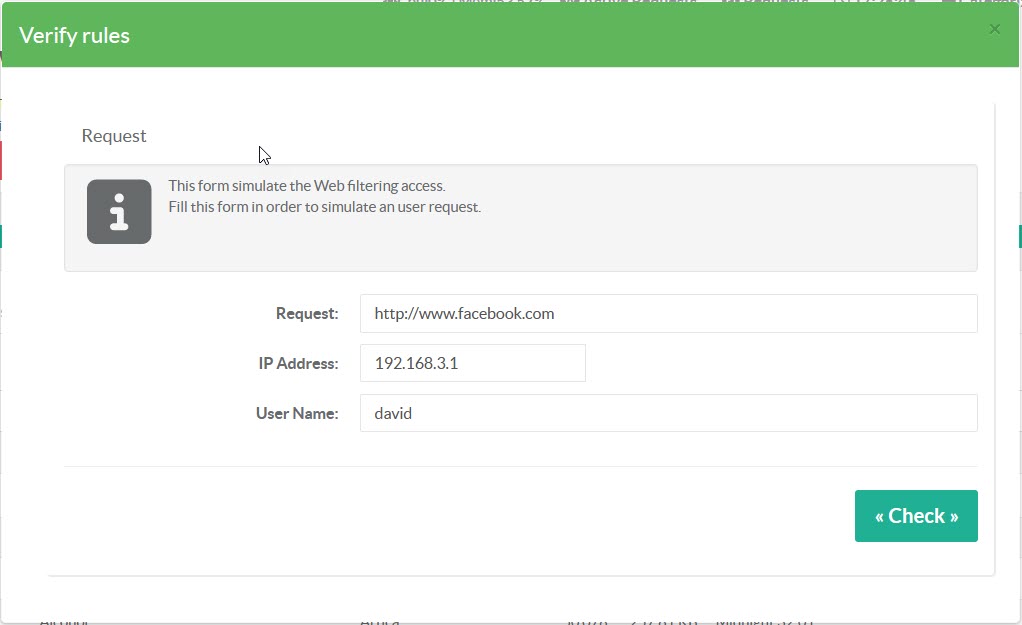
- In the form, fill at least the request and the IP address.
If your rules use Active Directory / LDAP group, add the login user name
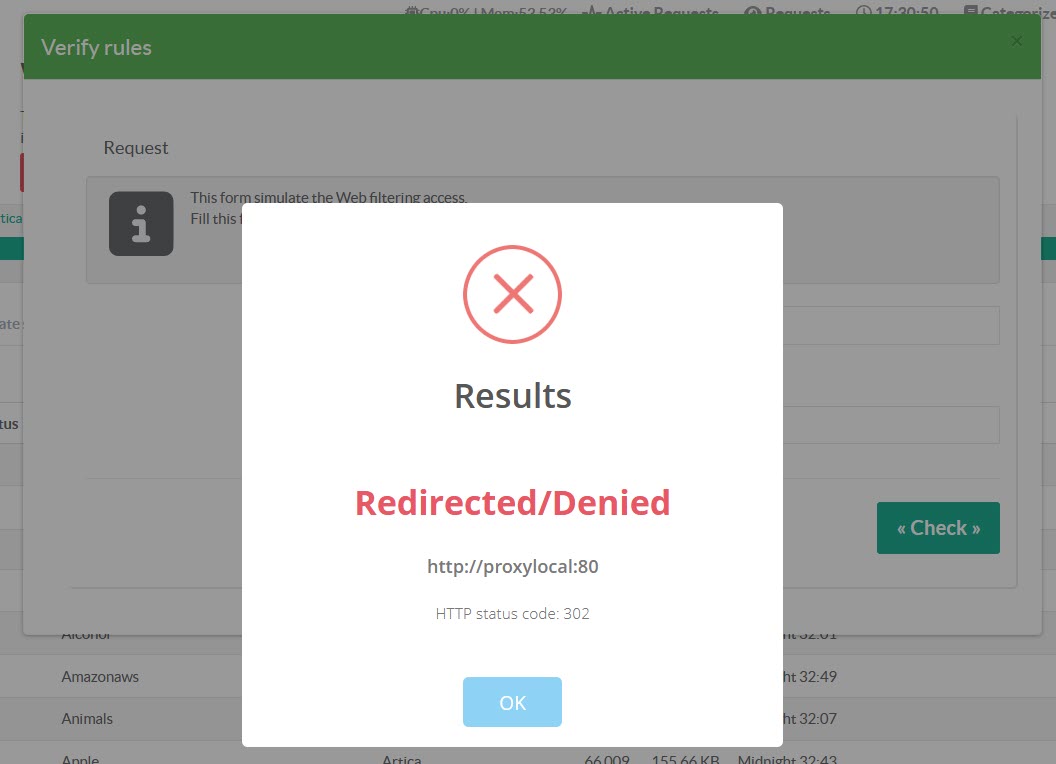
- If it is a deny rule, you will see a Redirected/Denied message
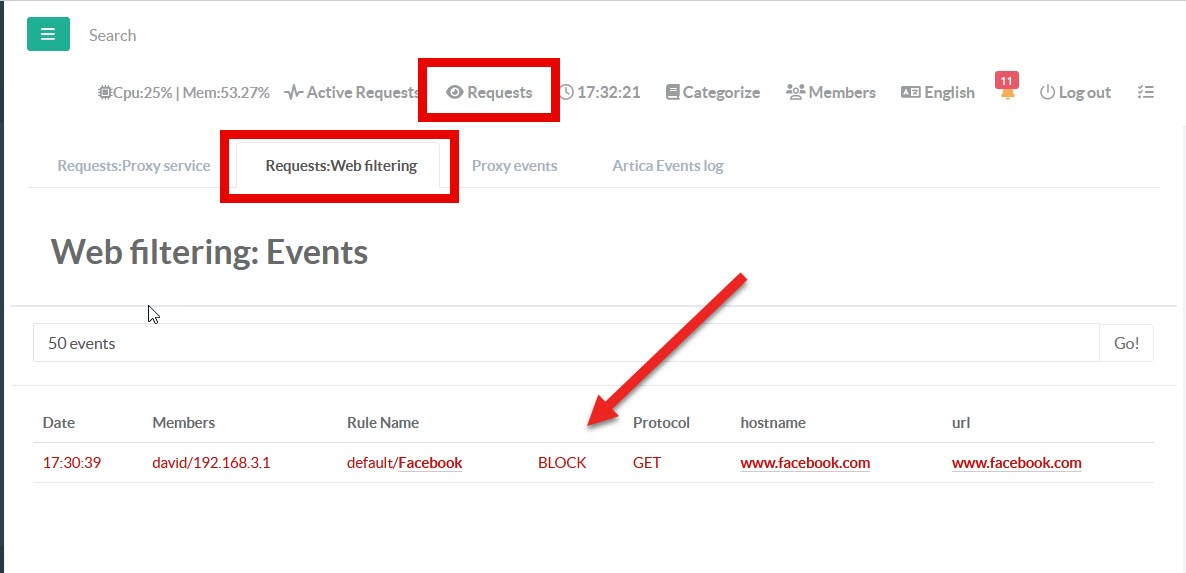
- On the top menu, click on Requests
- Click on Requests: Web Filtering
- You should see your simulation if the request is a denied request