In order to understand the power of using ACLs, we will develop a technical need that can be justified in many networks
¶ A concrete example
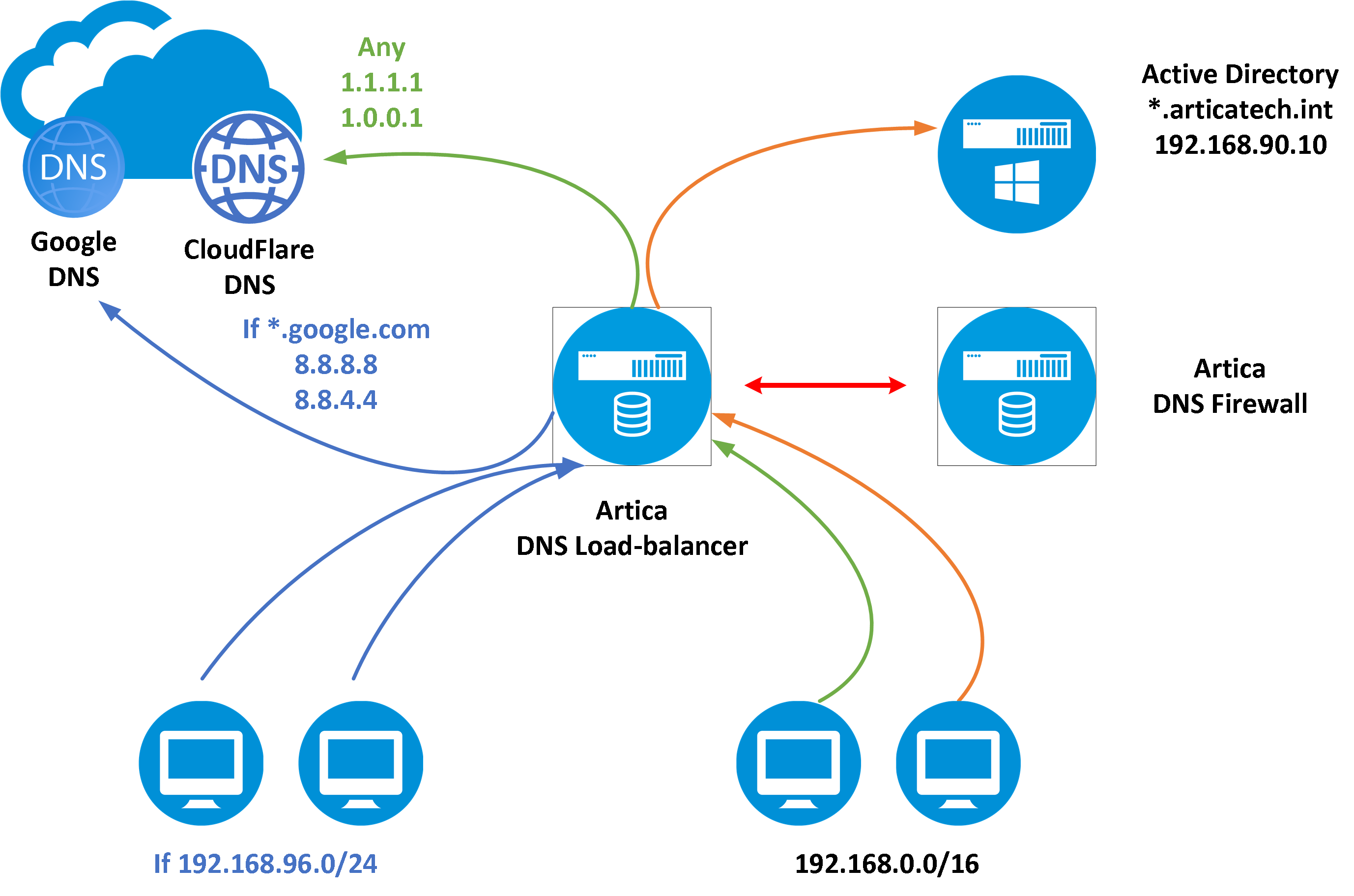
In this example, we want to produce the following DNS routing :
- The network 192.168.96.0/24, must use Google DNS in load-balancing mode for the domain google.com or CloudFlare DNS in load-balancing mode for other Internet DNS requests
- The network 192.168.0.0/16, which represents the entire network, must use the Artica DNS firewall for Internet DNS queries and the Active Directory server 192.168.90.10 for the domain articatech.int
- Of course, the Artica DNS Firewall service will use Cloudflare's services directly to avoid a loop
The ACLs in the DNS/Rules section will allow us to identify and merge the source and destination objects and DNS servers in order to build the rules that will ensure the main network objective
¶ Ensure the Google DNS routing.
Remember that we want to use Google's DNS servers only for the 192.168.96.0/24 network and for the google.com domain.
To do this, we will identify two groups:
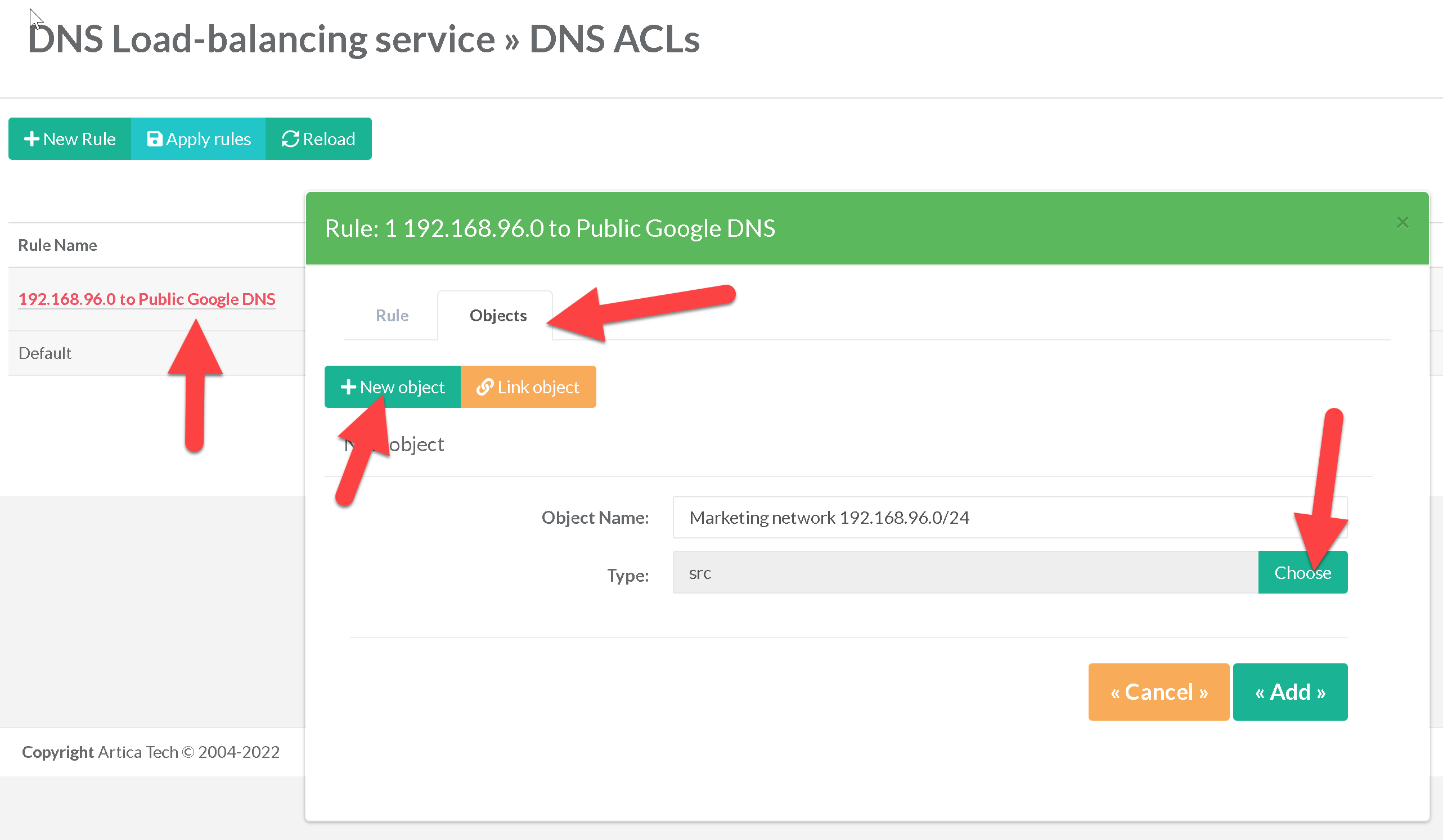
- The first step is to create a rule that “Balance DNS requests to”
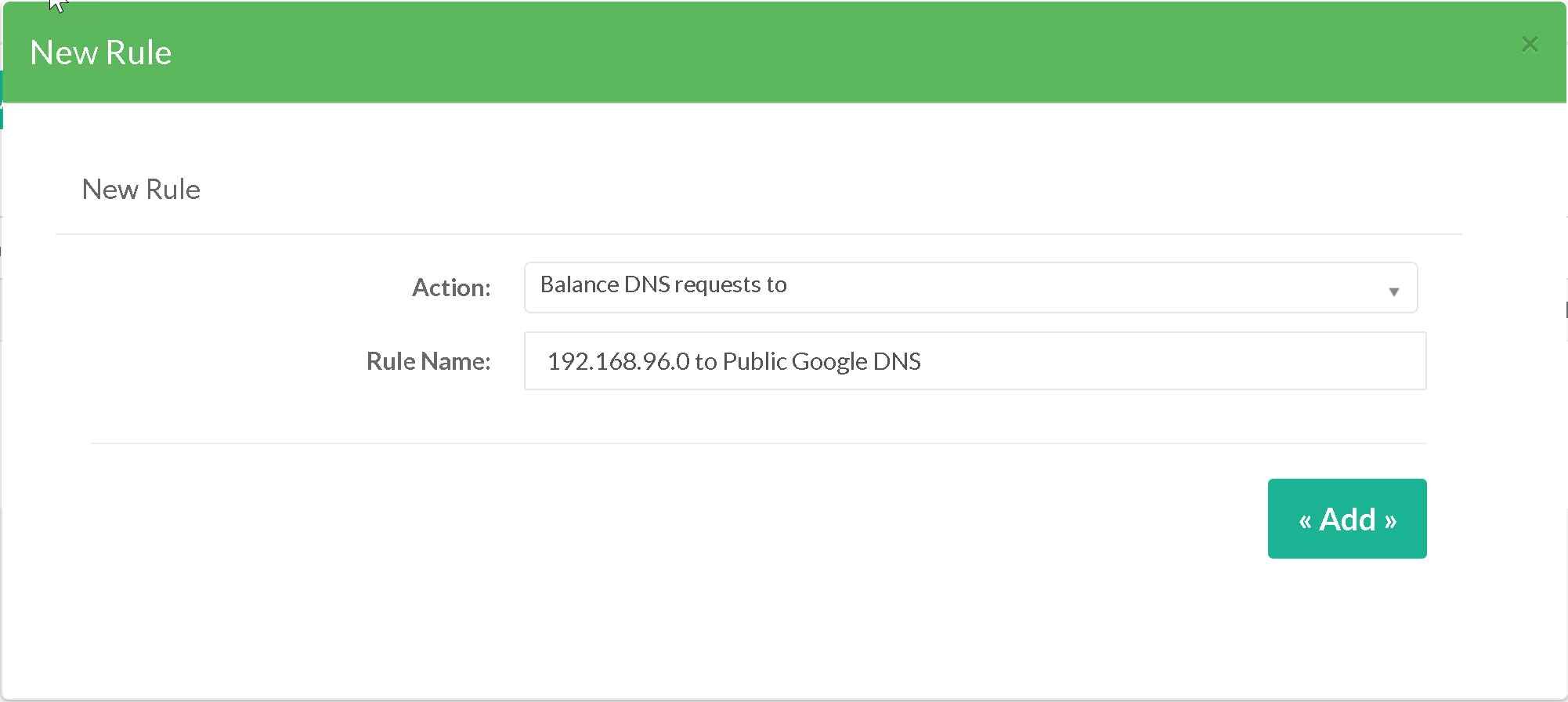
- When editing the new created rule, we use the Objects section
- We add a new “Source” type “src” object that will include our source network.
- We add a new “Destination domain” object with google.com
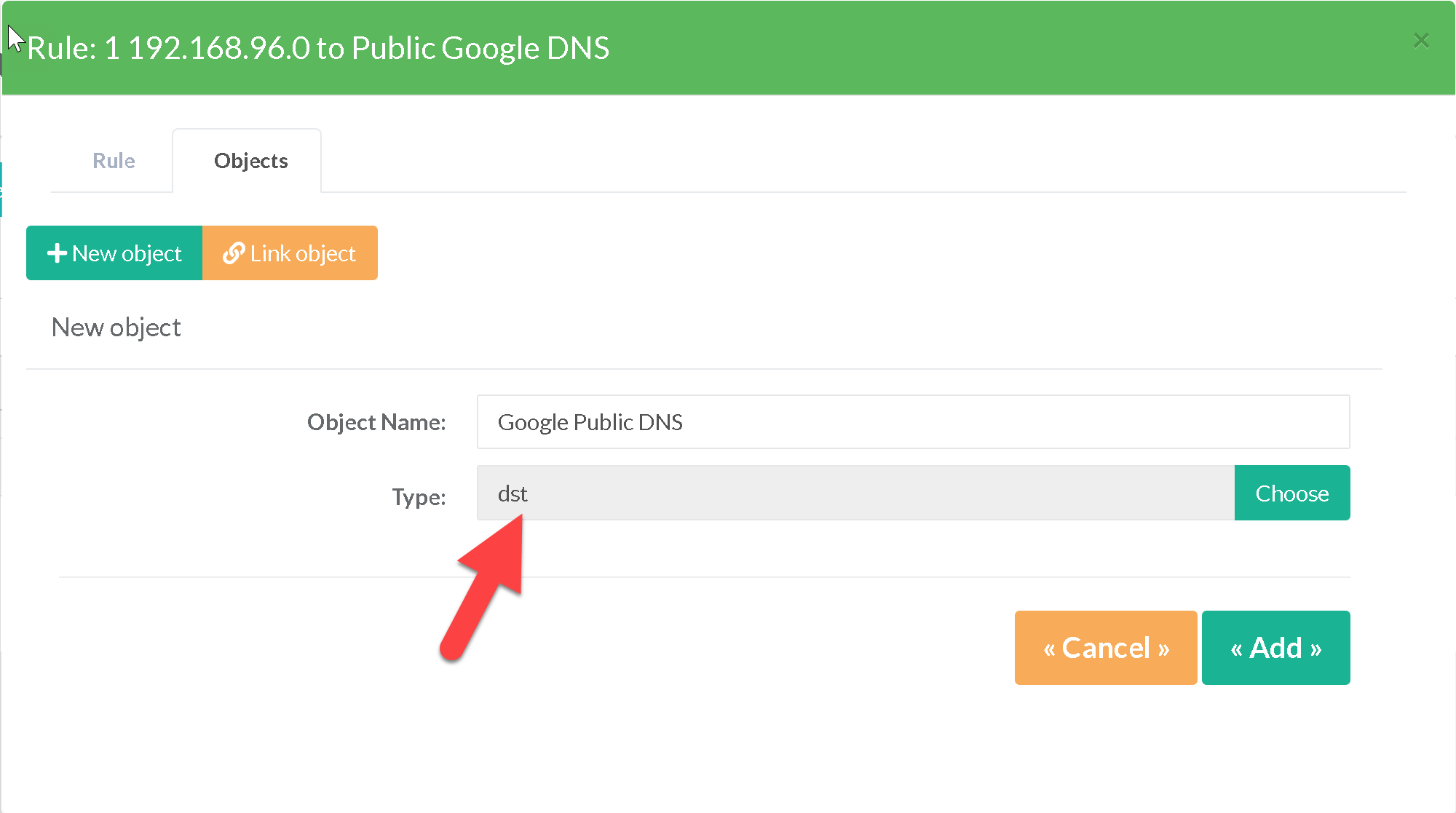
- Finally, we add an object “Destination Adresses” “dst” that will list the Google Public DNS servers
- To conclude, the 3 objects constitute the rule to use the google DNS servers for our source network.
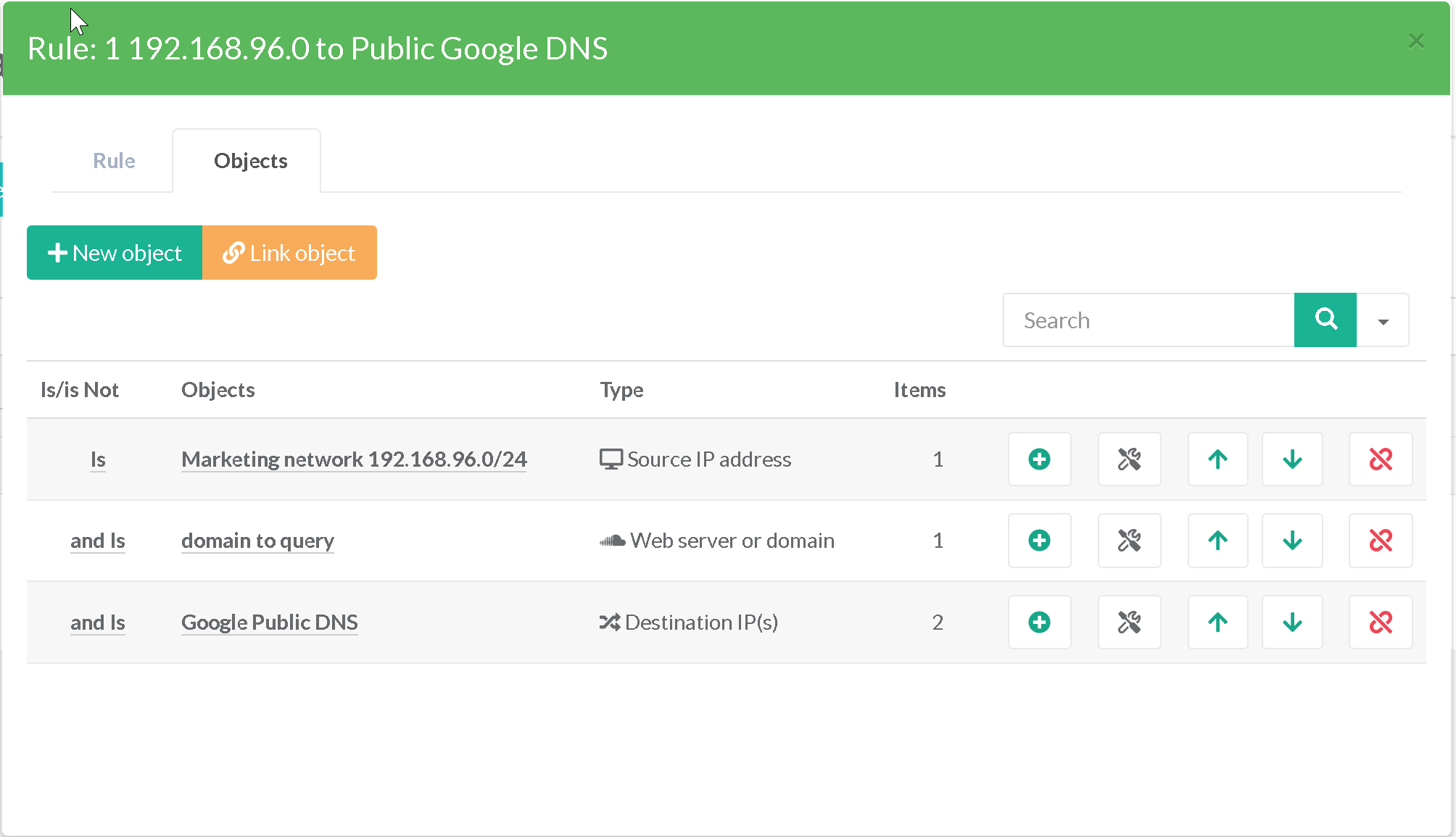
The table of rules describes each rule so that we understand all the added sets
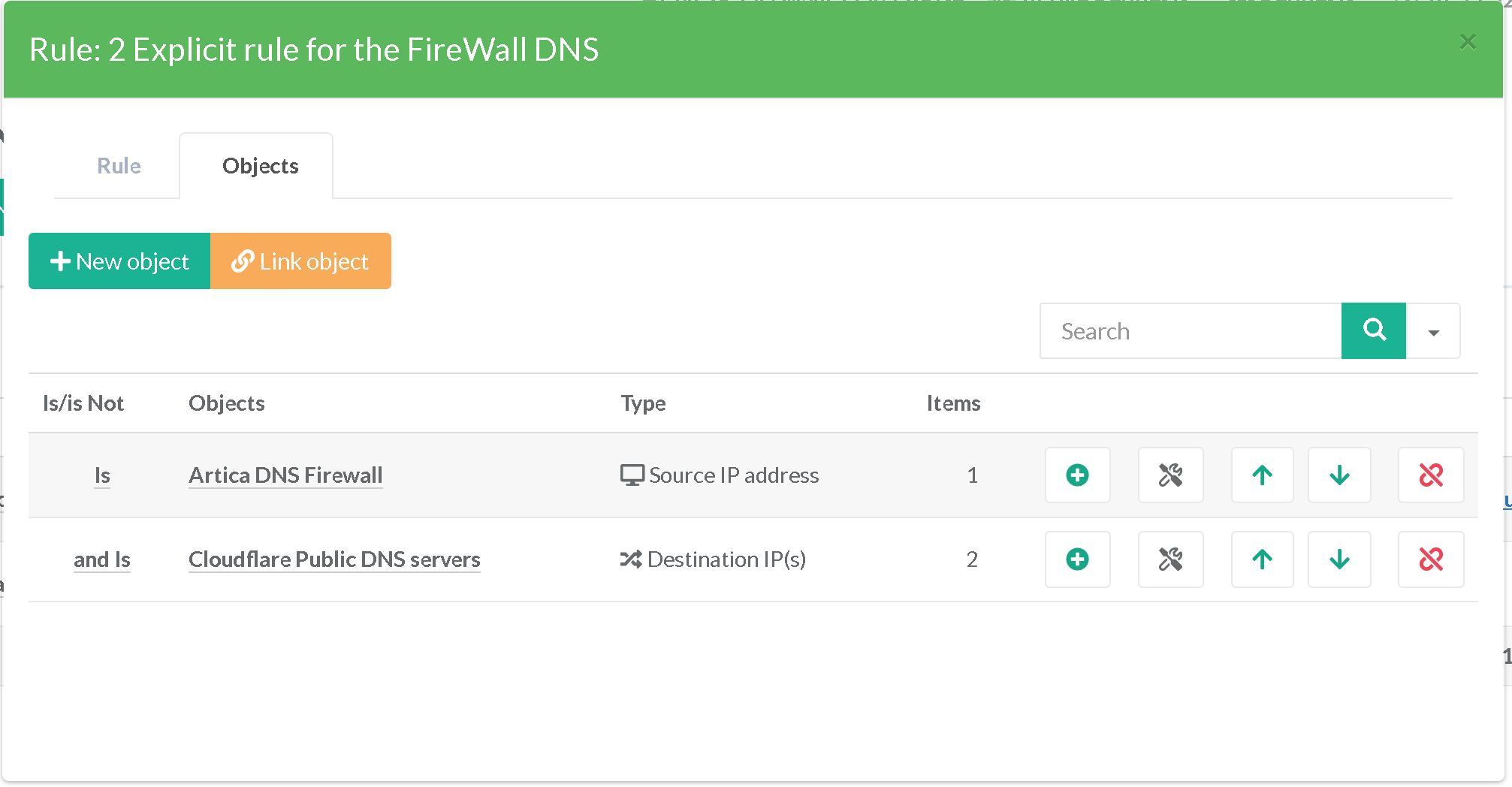
¶ Prevent the loop for the Artica DNS FireWall
In our approach, we have implemented Artica's DNS FireWall.
This one allows us to evaluate the reputation and security of DNS exchanges. It has the address 192.168.92.99.
In this context we create an explicit rule allowing this address to communicate directly with the CloudFlare public DNS servers
¶ Force using Active Directory server for articatech.int domain
Our network 192.168.0.0/16 must use the Active Directory DNS server 192.168.90.10 for the articatech.int domain.
More generally, we can omit the source, which then corresponds to all the nodes of the network
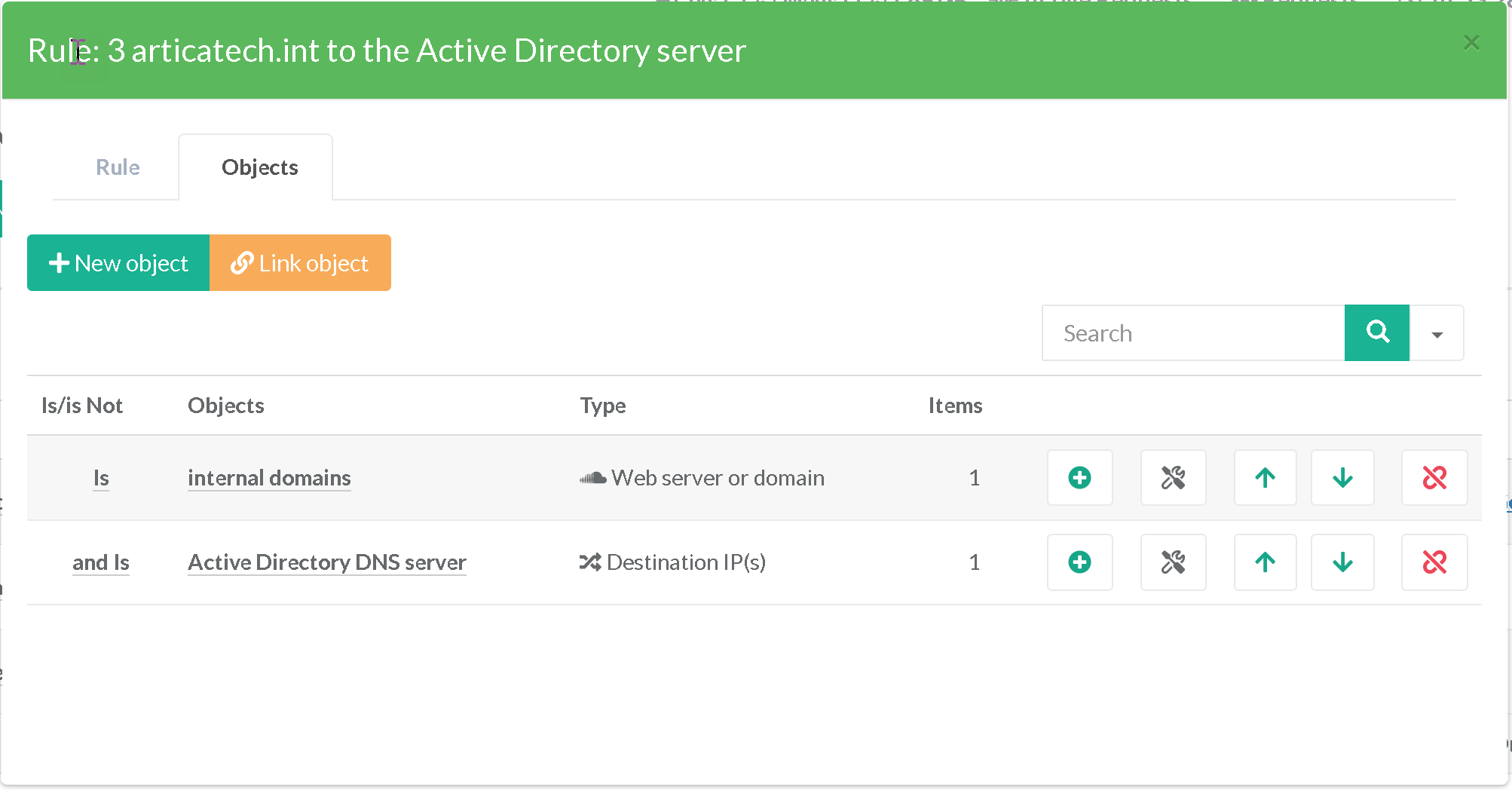
If we have a secondary Active Directory server, we could also add it, would result in putting both Active Directory servers in load balancing or fail-over
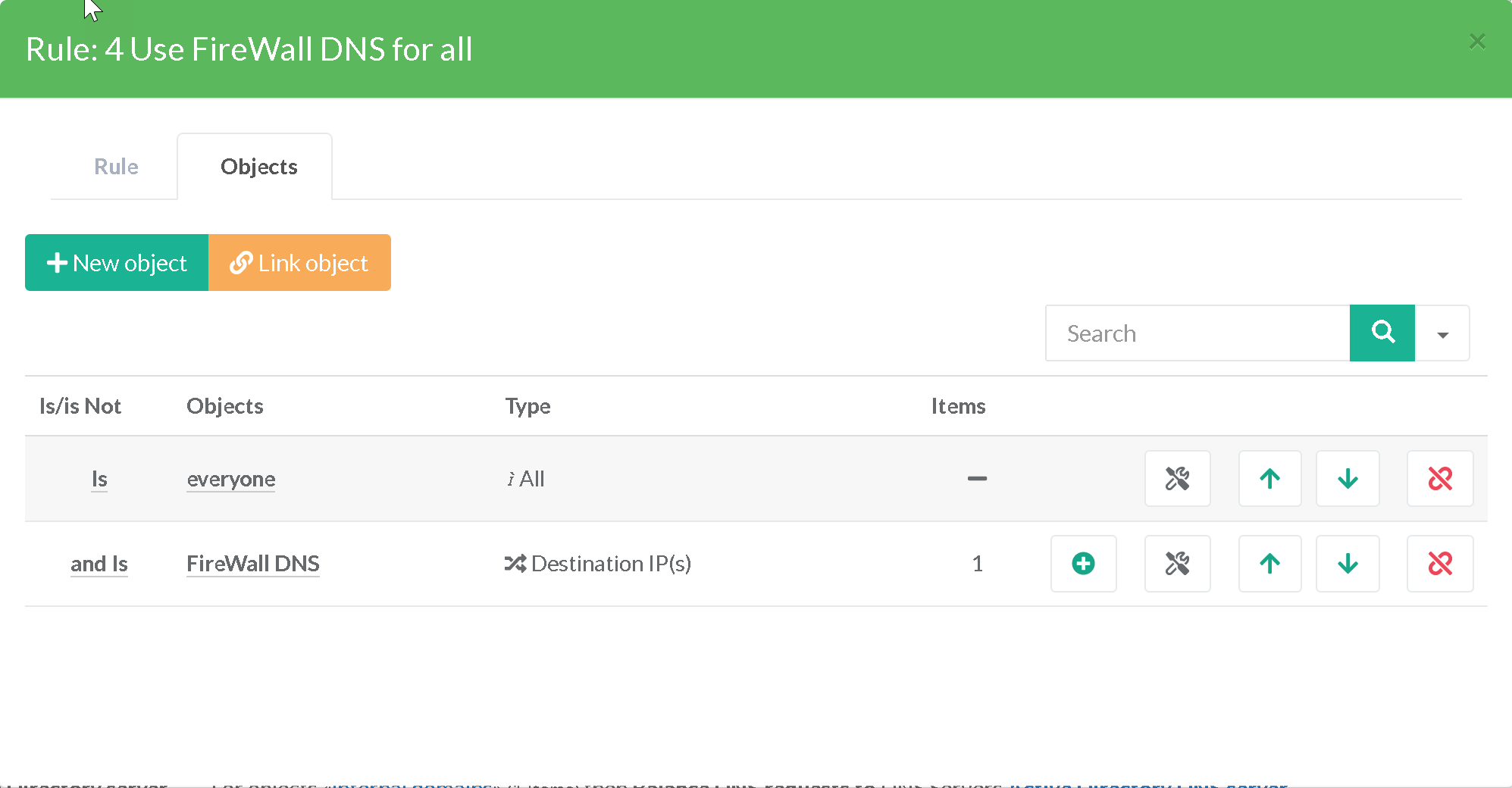
¶ Foreign domains, use the DNS Firewall
Finally, any unknown DNS requests will be processed by our DNS FireWall before using the public DNS servers
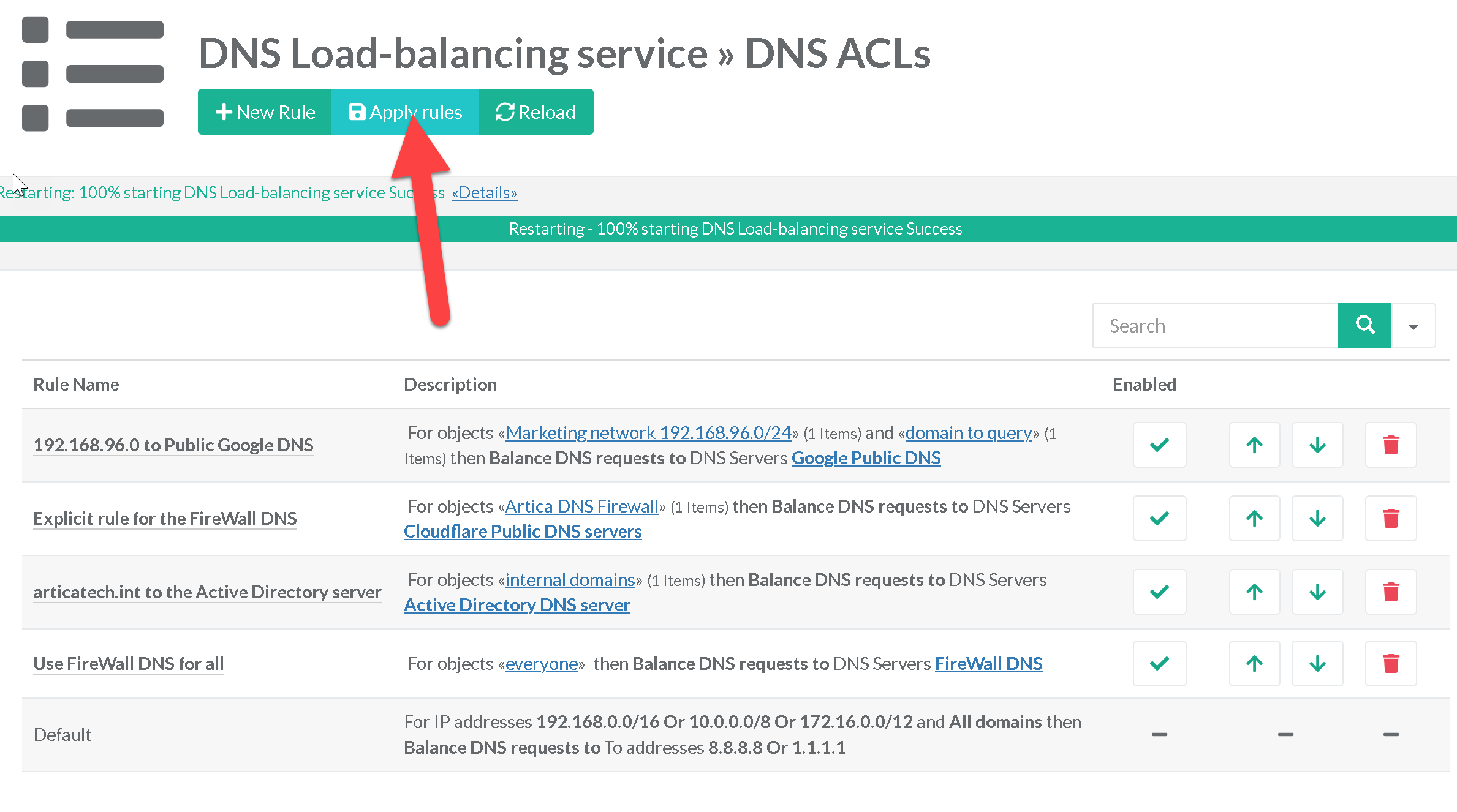
¶ To conclude
Click on Apply rules button to make rules in production mode.
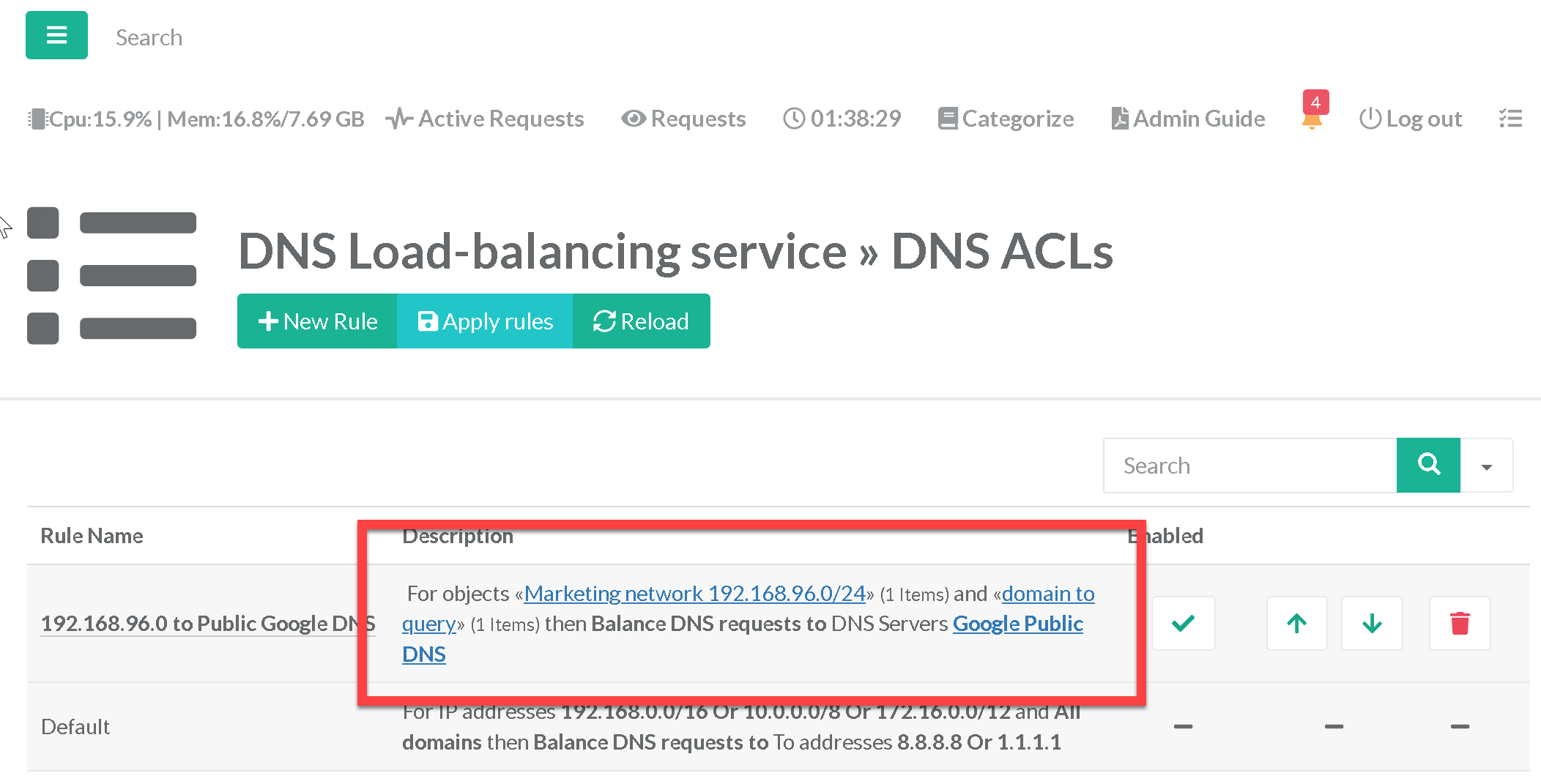
The rule table summarizes all our rules, the DNS load-balancer will understand the rules in the indicated order, we can then check the rules in operation in the real time access.