This feature detects packages in your mirror that are affected by known CVEs.
It automatically performs CVE scans after each repository synchronization and allows you to search for vulnerabilities by package name or CVE ID.
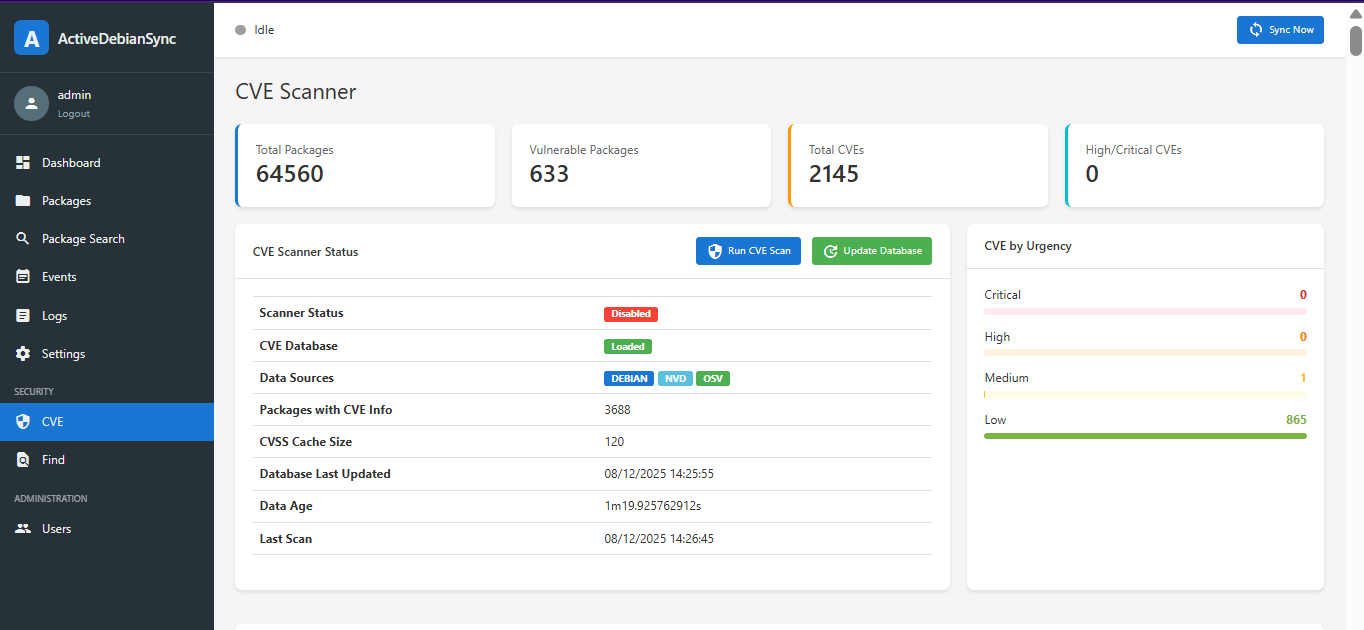
¶ Enable the CVE scanner
in your config.json:
{ "cve_scanner_enabled": true, //Enable/disable the CVE scanner "cve_scan_after_sync": true,// Automatically run CVE scan after repository sync "cve_cache_expiry_hours": 6, //Hours before CVE database cache expires and is refreshed "cve_nvd_enabled": true, //Enable NVD (NIST) integration for CVSS scores "cve_nvd_api_key": "",//Optional NVD API key for higher rate limits "cve_osv_enabled": true //Enable OSV.dev integration for additional CVE data}
¶ Command-lines
Update CVE Database
Download/refresh the CVE database from Debian Security Tracker:./activedebiansync cve update -config /path/to/config.json
Run CVE Scan
Scan all packages in the repository for vulnerabilities:
- Scan all releases, components, and architectures :
./activedebiansync cve scan -config /path/to/config.json - Scan specific release:
./activedebiansync cve scan -config /path/to/config.json -release bookworm - Scan specific component:
./activedebiansync cve scan -config /path/to/config.json -component main - Scan specific architecture:
./activedebiansync cve scan -config /path/to/config.json -arch amd64 - Include package details in output:
./activedebiansync cve scan -config /path/to/config.json -packages
Check Scanner Status
View the current status of the CVE scanner: ./activedebiansync cve status -config /path/to/config.json
Search Package CVEs
Get CVE information for a specific package:
- Search for package CVEs:
./activedebiansync cve package -config /path/to/config.json -name openssl - Search for specific release:
./activedebiansync cve package -config /path/to/config.json -name openssl -release bookworm
Search by CVE ID
Search for a specific CVE:
./activedebiansync cve search -config /path/to/config.json -cve CVE-2024-12345
Get Summary
Get a summary of all vulnerabilities:
./activedebiansync cve summary -config /path/to/config.json
¶ REST API Endpoints
When the REST API is enabled, the following CVE endpoints are available:
GET /api/cve/status
Get CVE scanner status.
Response:
{ "enabled": true, "initialized": true, "packages_count": 1234, "last_updated": "2025-12-08T12:00:00Z", "data_age_hours": 2.5, "scan_after_sync": true}
POST /api/cve/update
Force update of CVE database.
Response:
{ "status": "success", "message": "CVE data updated successfully", "packages_count": 1234 }
POST /api/cve/scan
Run a CVE scan.
Query Parameters:
release(optional): Filter by release (e.g., bookworm)component(optional): Filter by component (e.g., main)architecture(optional): Filter by architecture (e.g., amd64)packages(optional): Include package details (true/false)
Response:
{ "scan_time": "2025-12-08T12:00:00Z", "total_packages": 63463, "vulnerable_packages": 625, "total_cves": 2082, "critical_cves": 0, "high_cves": 5, "medium_cves": 42, "low_cves": 156, "unassigned_cves": 1879}
GET /api/cve/summary
Get vulnerability summary.
Response:
{ "total_packages": 63463, "vulnerable_packages": 625, "total_cves": 2082, "by_urgency": { "critical": 0, "high": 5, "medium": 42, "low": 156, "unassigned": 1879 }}
GET /api/cve/package
Get CVE information for a specific package.
Query Parameters:
name(required): Package namerelease(optional): Filter by release
Response:
{ "package": "openssl", "version": "3.0.17-1~deb12u2", "release": "bookworm", "component": "main", "architecture": "amd64", "cves": [ { "cve_id": "CVE-2025-9232", "description": "An application using the OpenSSL HTTP client API...", "status": "resolved", "urgency": "not yet assigned", "fixed_version": "3.0.17-1~deb12u3" } ], "total_cves": 3, "critical": 0, "high": 0, "medium": 0, "low": 0, "unassigned": 3}
GET /api/cve/search
Search by CVE ID.
Query Parameters:
cve(required): CVE ID (e.g., CVE-2024-12345)
Response:
{ "cve_id": "CVE-2024-12345", "description": "Vulnerability description...", "affected_packages": ["package1", "package2"], "status": "open", "urgency": "high"}
¶ Used CVE sources:
- Debian Security Tracker:
Primary CVE data for Debian packages (vulnerabilities, status, urgency, fixed versions)
Downloaded first, provides the main vulnerability list for all Debian packages
https://security-tracker.debian.org/tracker/data/json - NVD (NIST):
CVSS scores (v3.1/v3.0/v2.0) and severity ratings
Queried on-demand for individual CVEs when CVSS score not in cache
https://services.nvd.nist.gov/rest/json/cves/2.0 - OSV.dev
Bulk Debian vulnerability database with CVSS data
Downloaded as a zip file during update, CVSS scores are extracted and cached
https://osv-vulnerabilities.storage.googleapis.com/Debian/all.zip